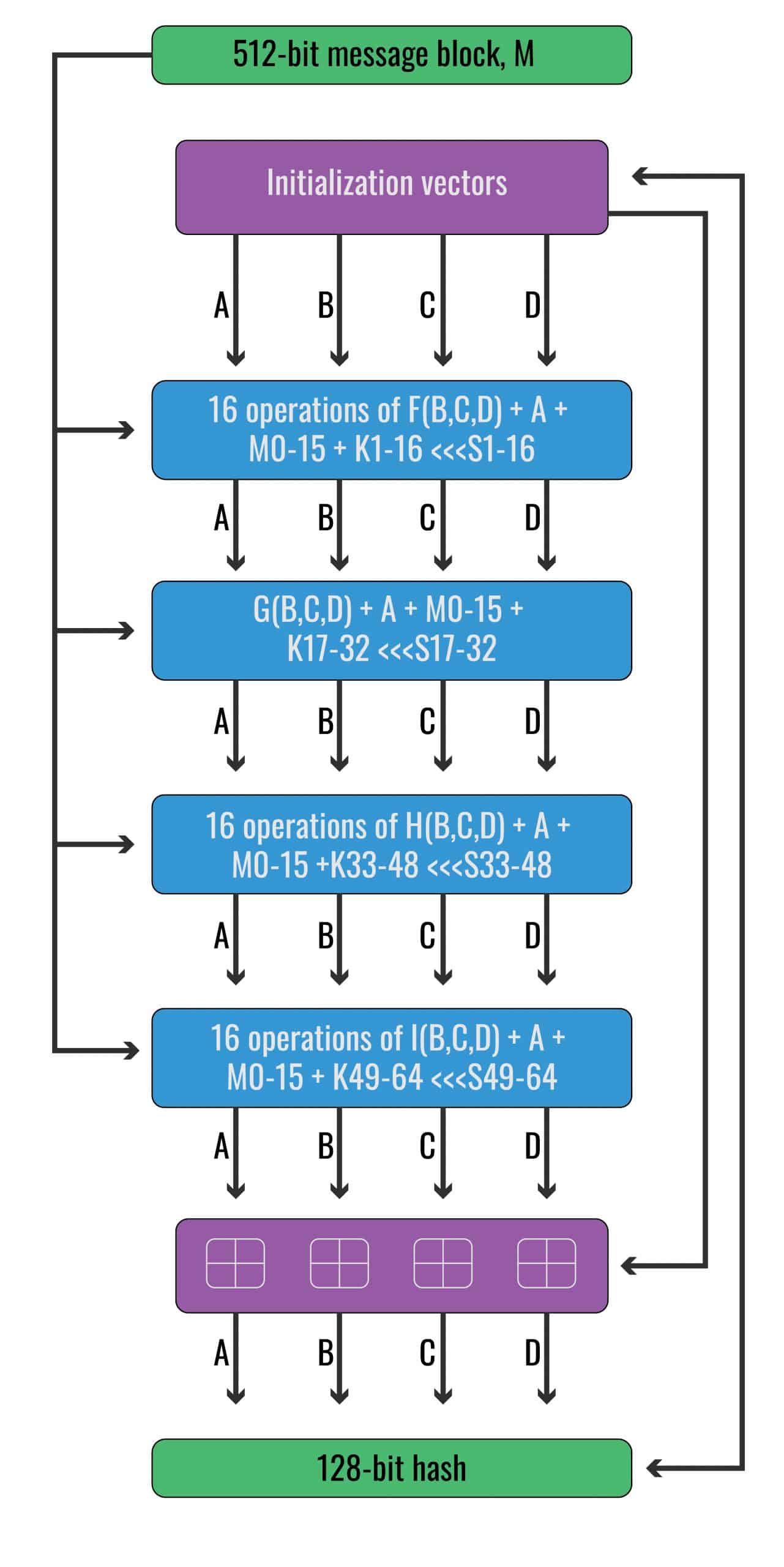
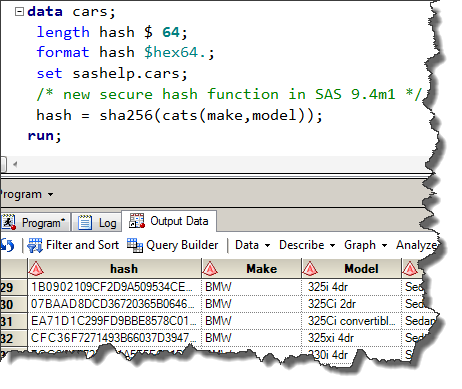
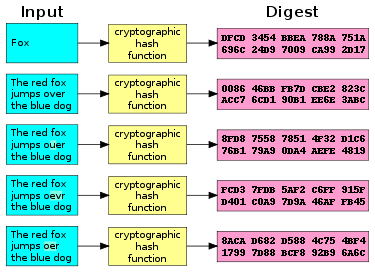
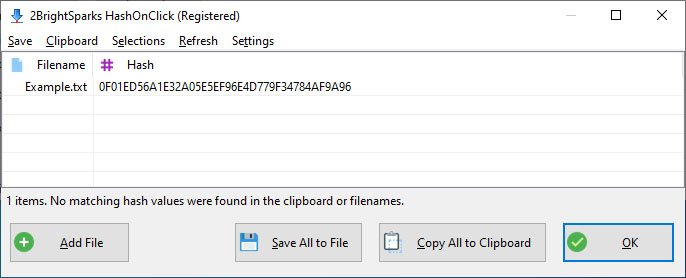
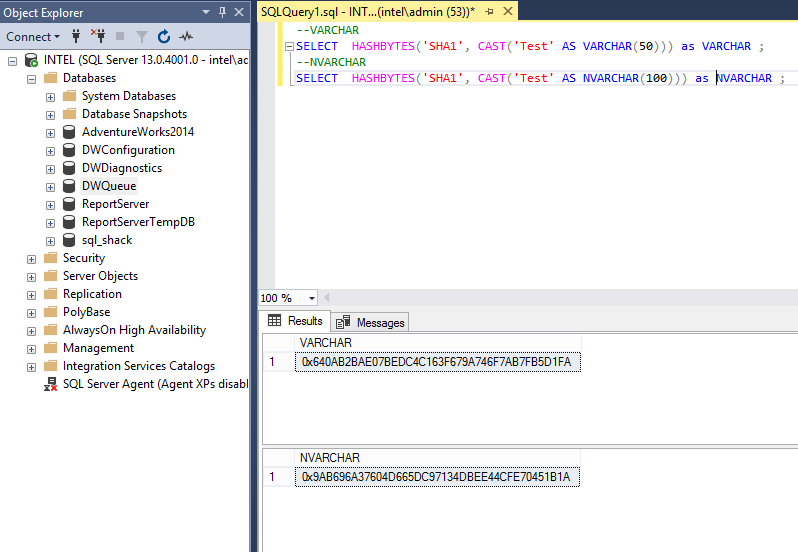
Increase the maximum length of a reserve password hash for the RSA Authentication Agent 7.x for Wind... - RSA Community - 2299
Implementing the sha256 and md5 hash functions in C | by Jean-Baptiste Terrazzoni | My 42 stories | Medium
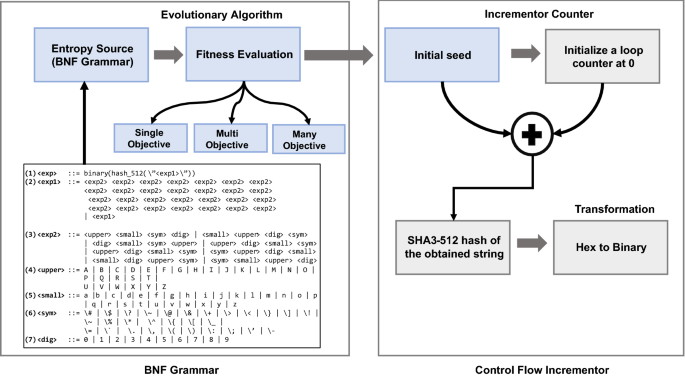
Design of a cryptographically secure pseudo random number generator with grammatical evolution | Scientific Reports