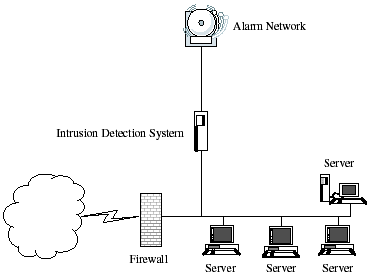
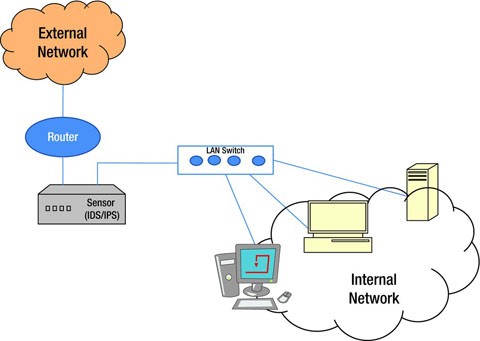
A survey on intrusion detection system: feature selection, model, performance measures, application perspective, challenges, and future research directions | SpringerLink
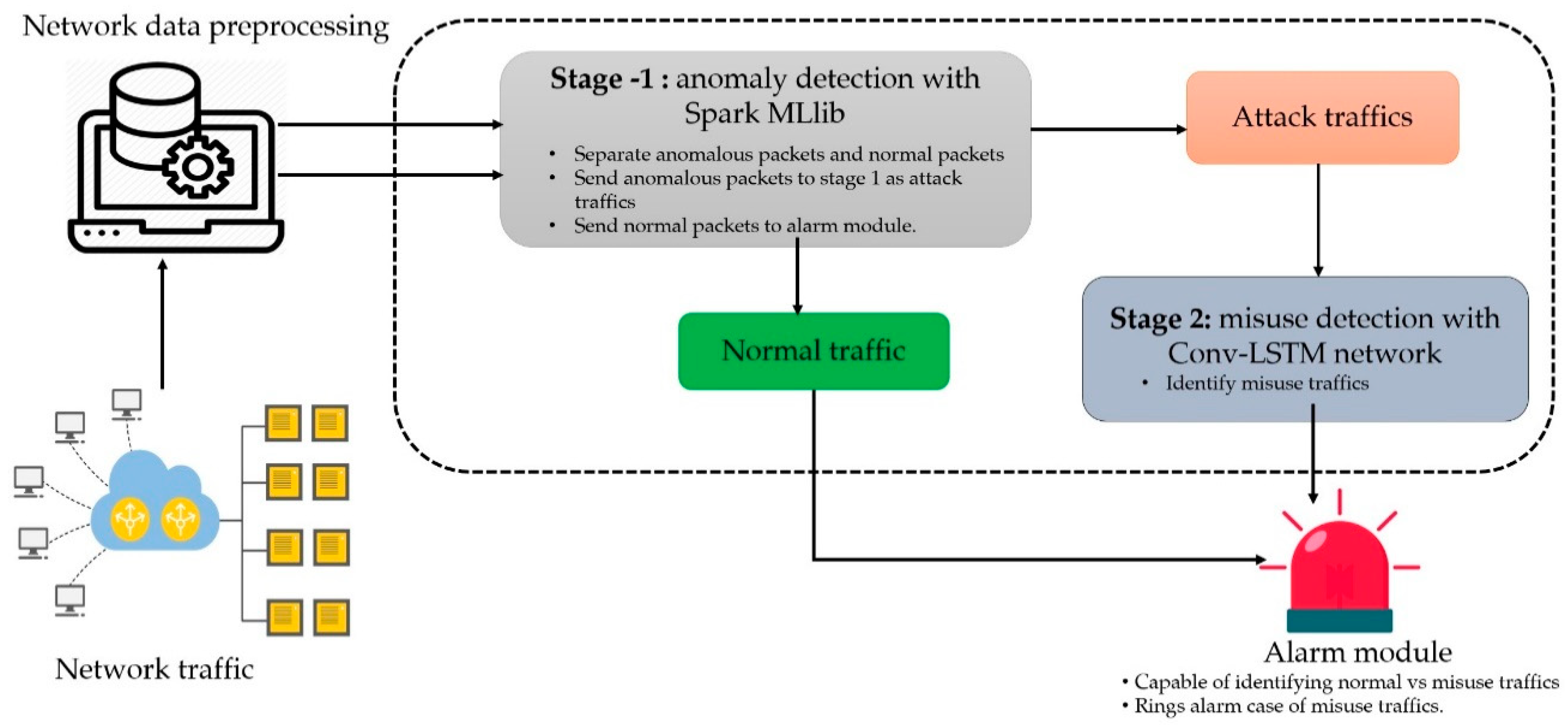
Symmetry | Free Full-Text | A Scalable and Hybrid Intrusion Detection System Based on the Convolutional-LSTM Network | HTML
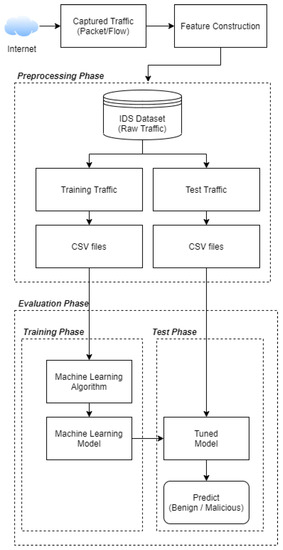
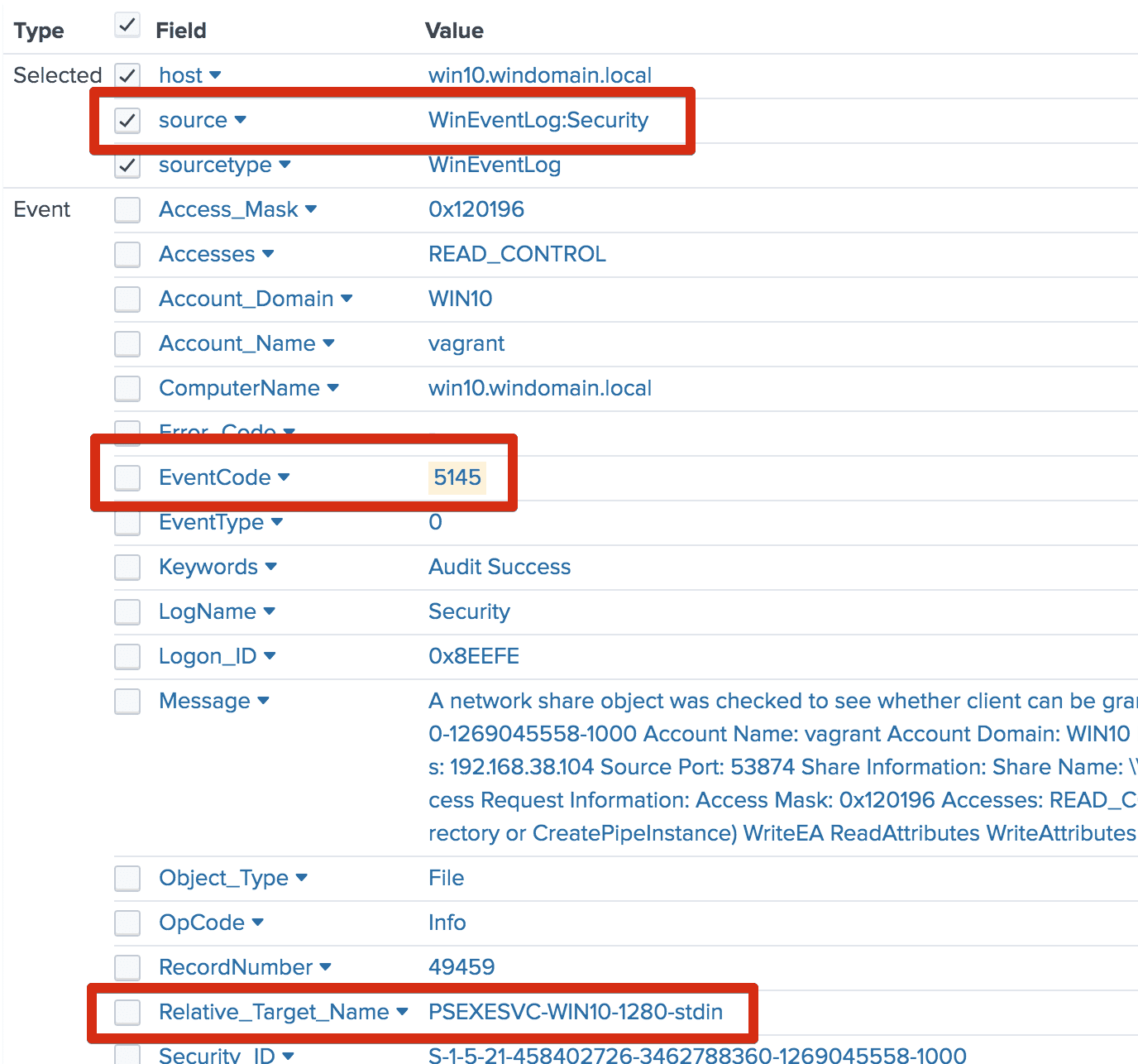
Applied Sciences | Free Full-Text | Generating Network Intrusion Detection Dataset Based on Real and Encrypted Synthetic Attack Traffic | HTML

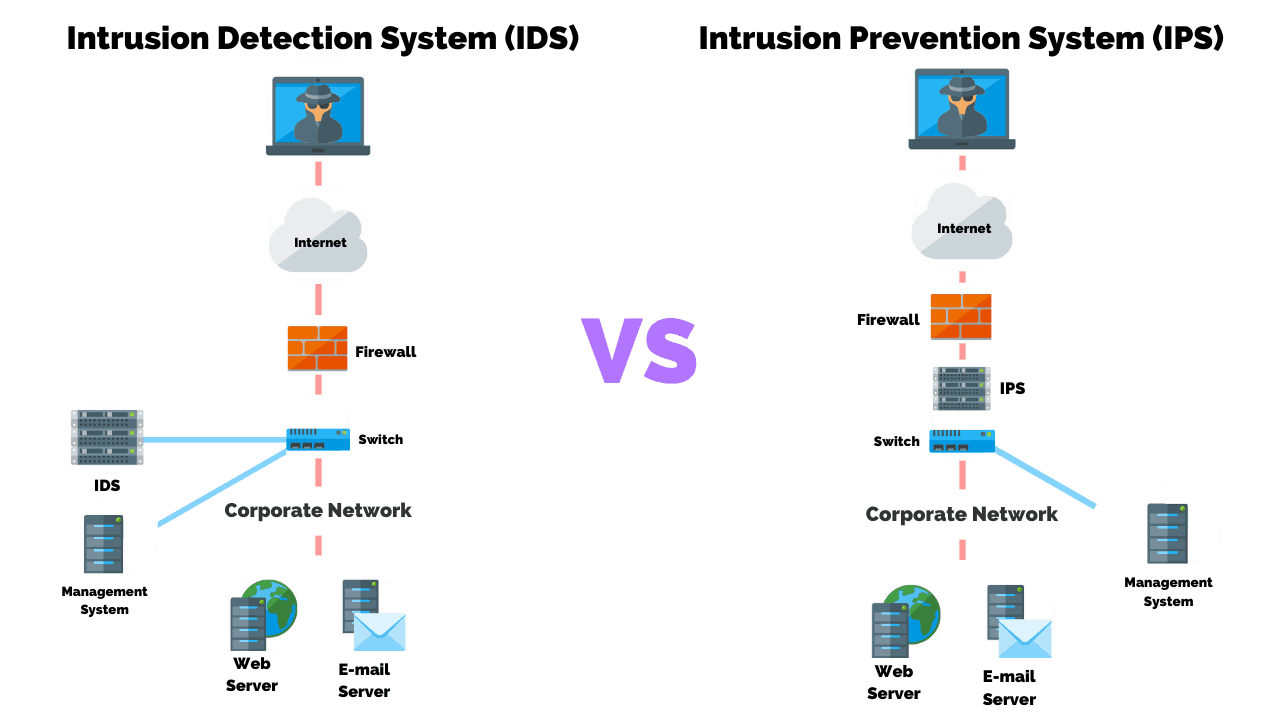
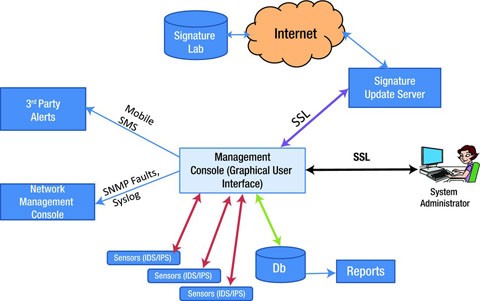
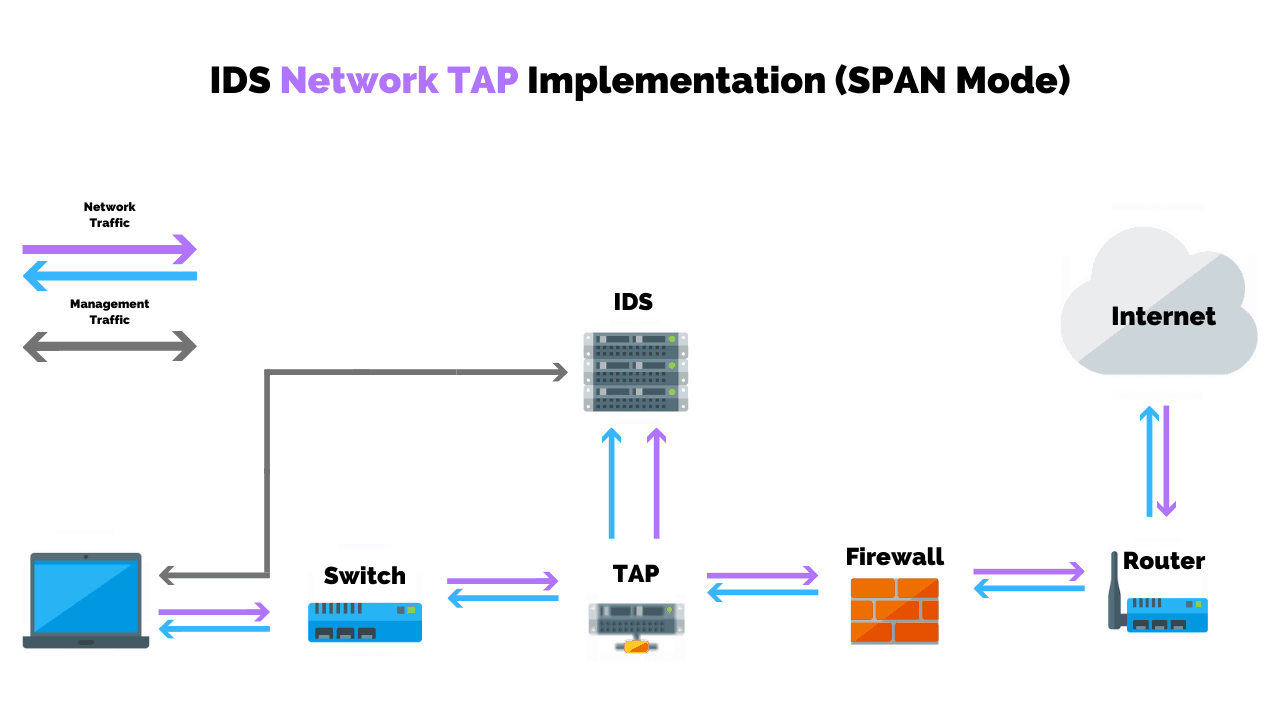
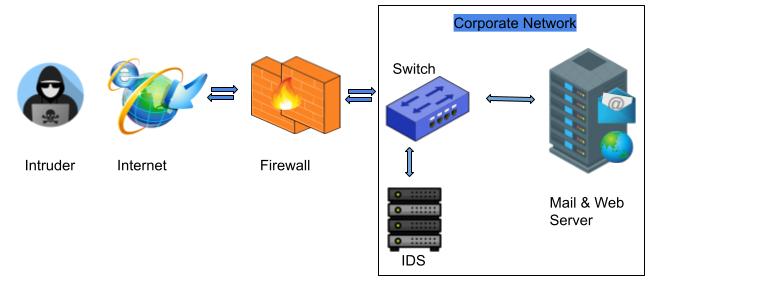
What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security

What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security

What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security