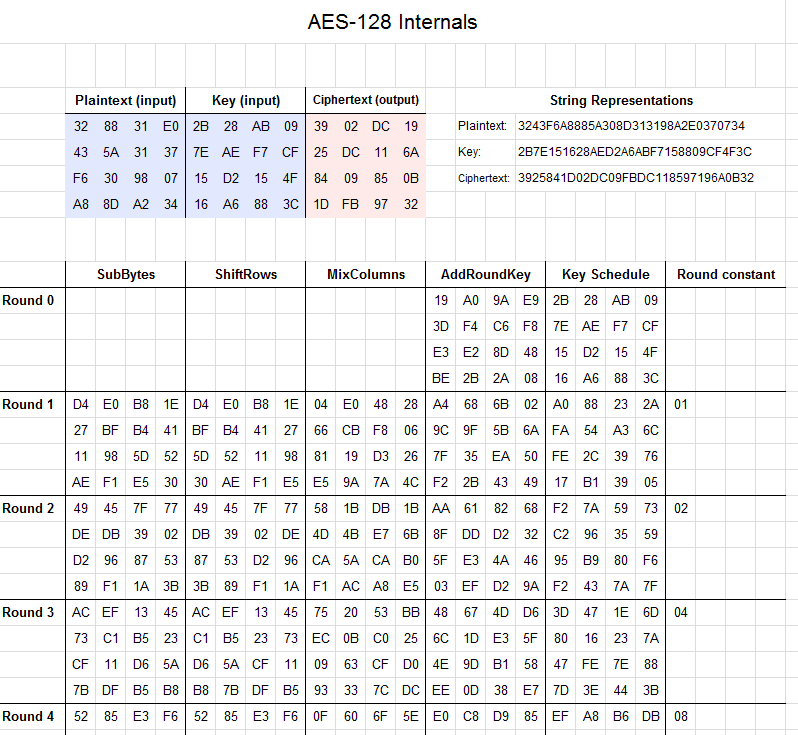
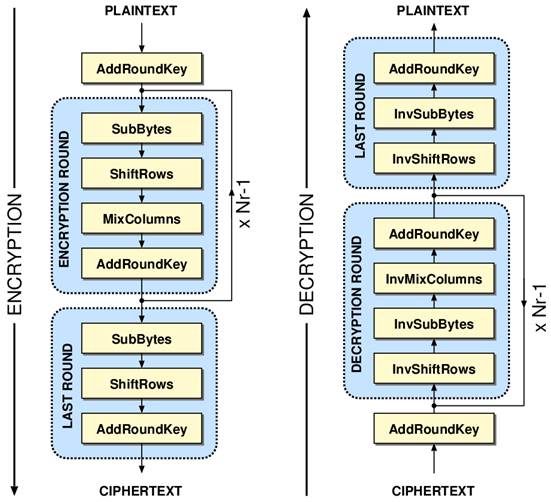
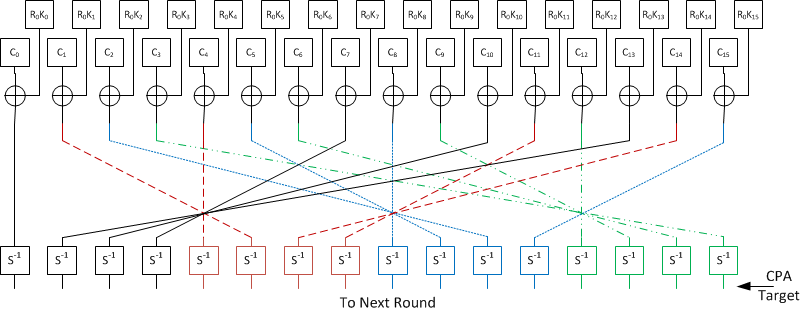
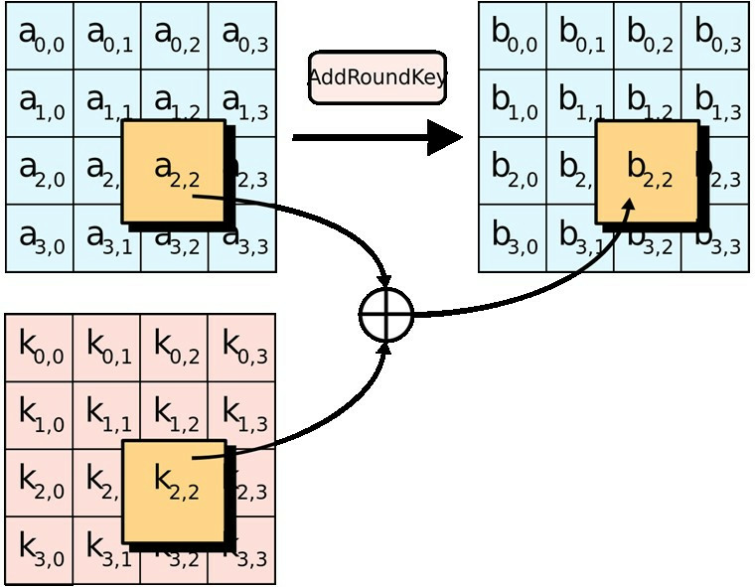
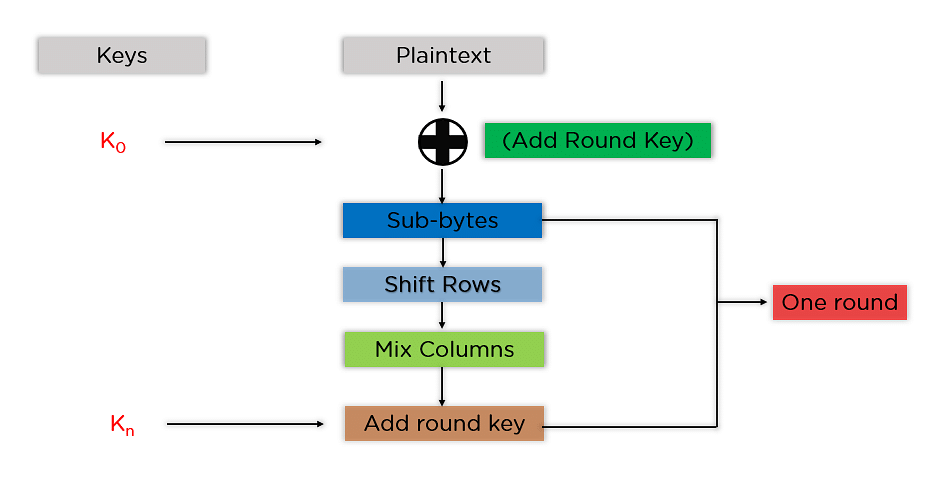
Development of key-dependent dynamic S-Boxes with dynamic irreducible polynomial and affine constant - Praveen Agarwal, Amandeep Singh, Adem Kilicman, 2018

AES Encryption 256 Bit. The encryption standard to rule them… | by Cory Maklin | Towards Data Science

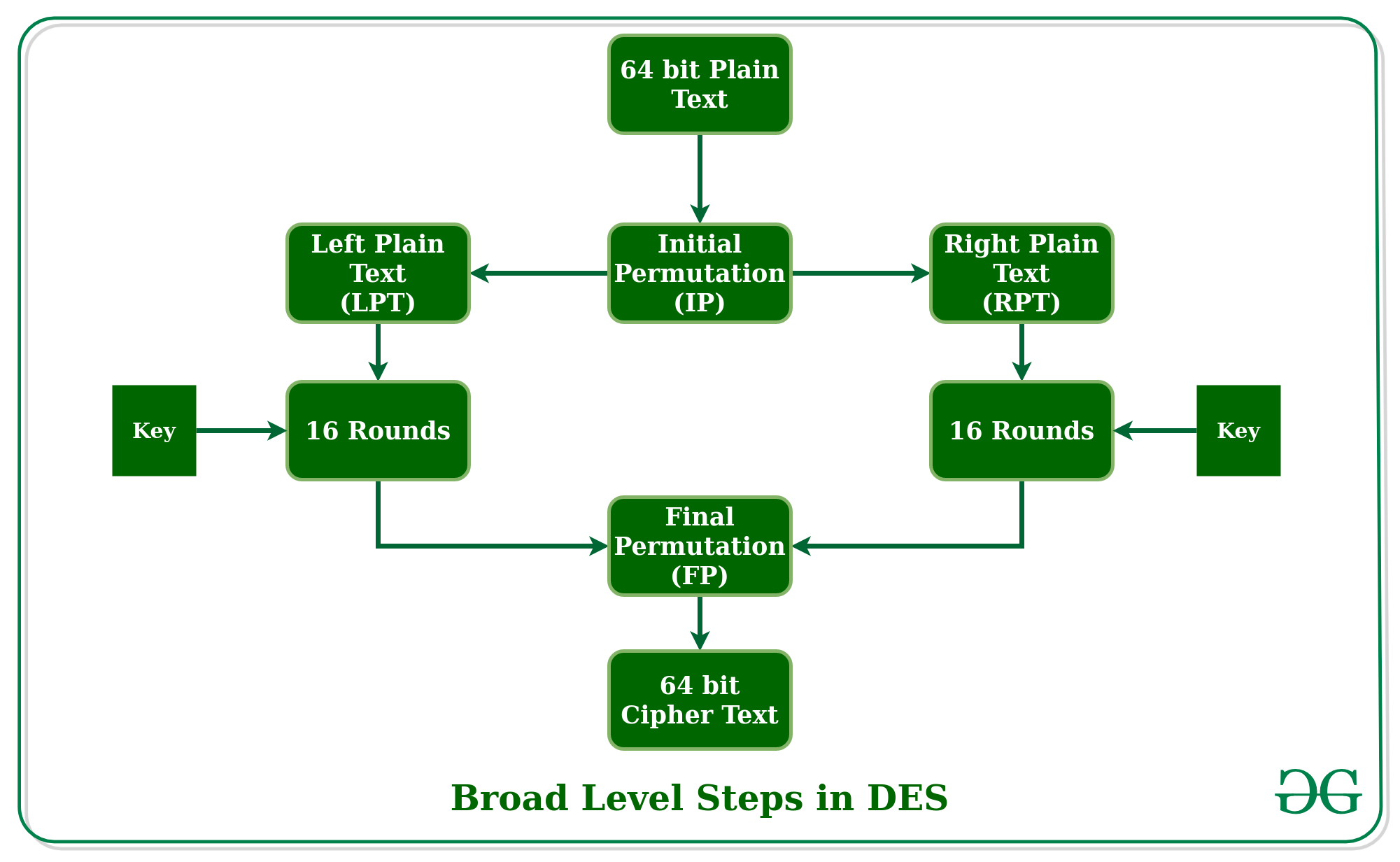
A Comparison of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention

AES Encryption Function ontools | AES Encryption Free Online Tool Supports 128 192 256 Bits... | #1 BEST - AES Encryption Online - ᐈ AES Encryption and Decryption Online Tool | Online AES Encryption and Decryption function ontools
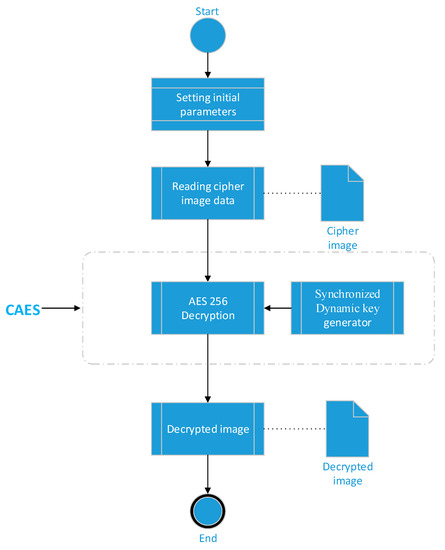
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm | HTML
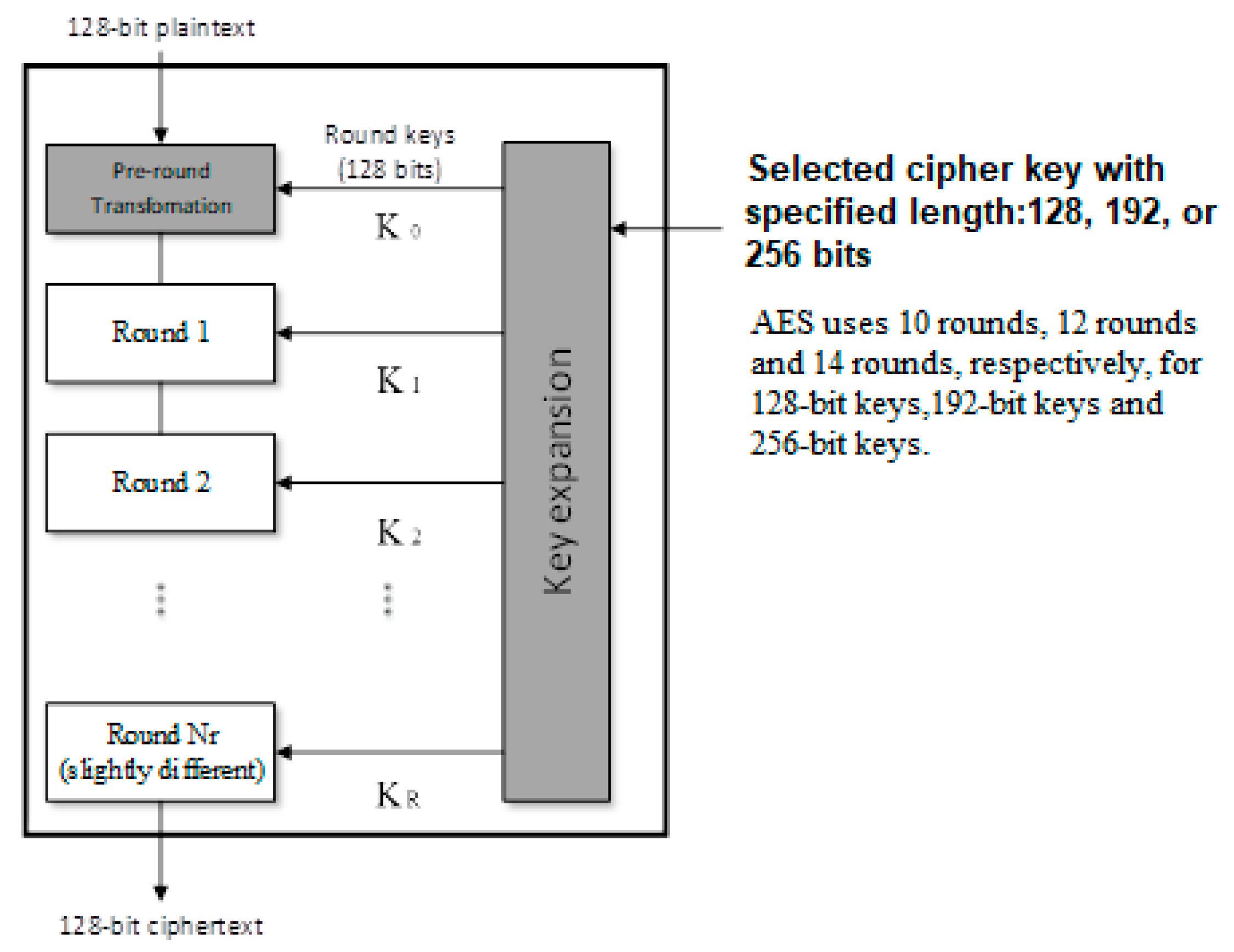
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm | HTML