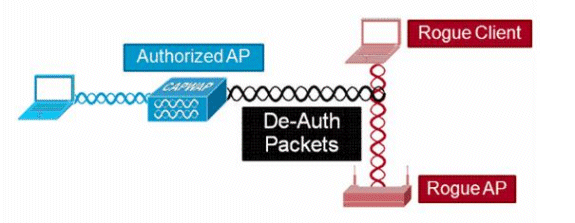
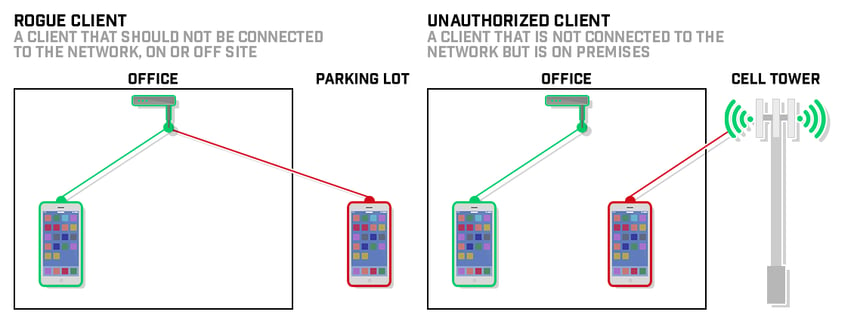
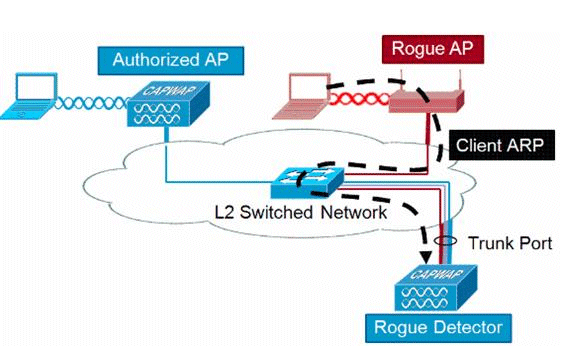
Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press
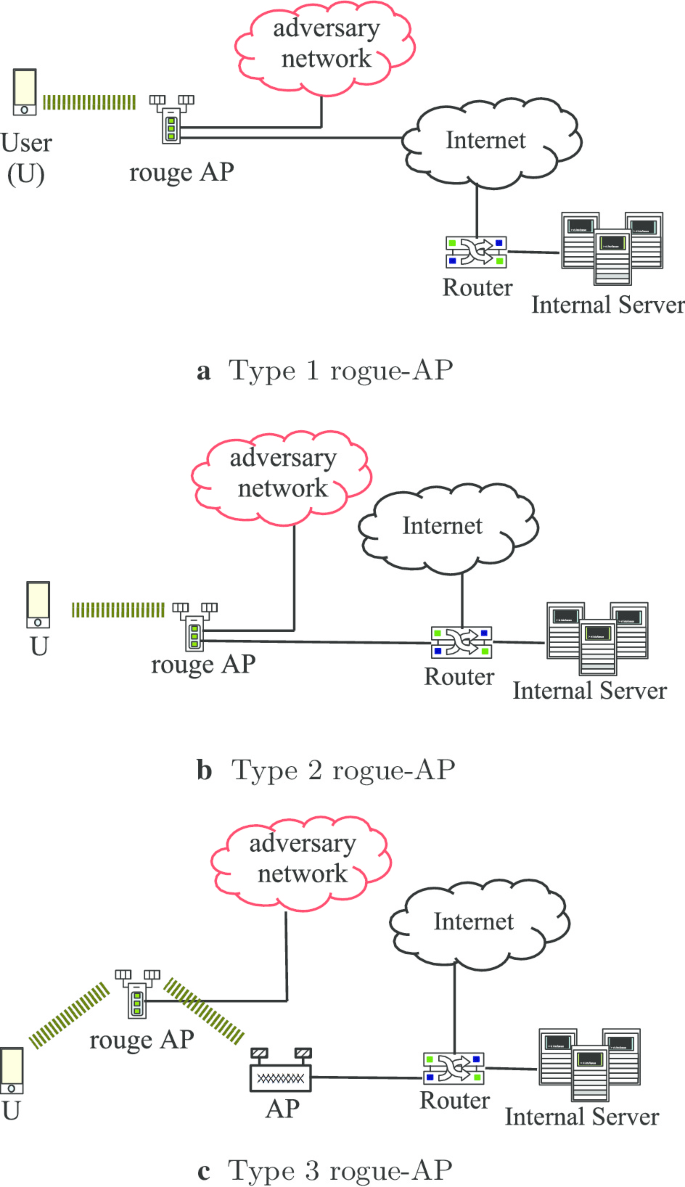
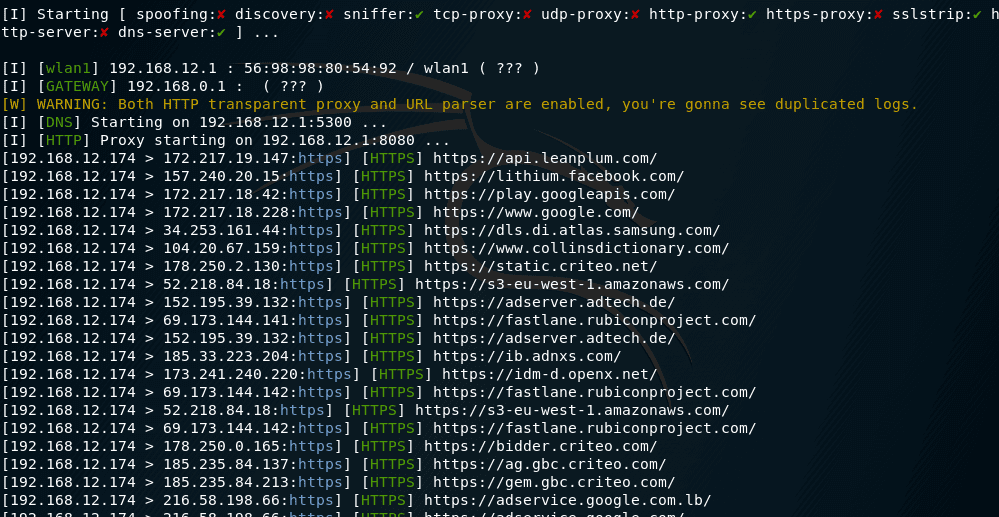
Client-side rogue access-point detection using a simple walking strategy and round-trip time analysis | EURASIP Journal on Wireless Communications and Networking | Full Text
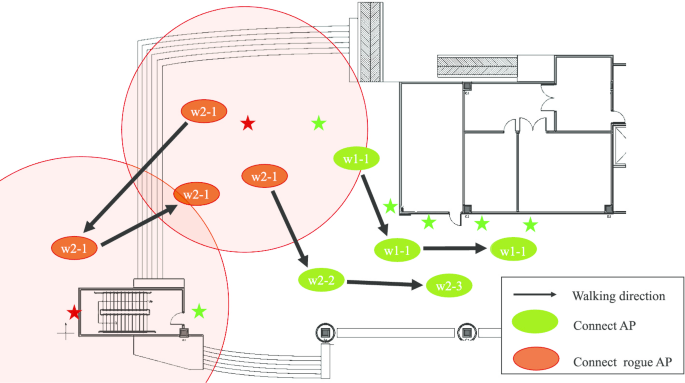
Client-side rogue access-point detection using a simple walking strategy and round-trip time analysis | EURASIP Journal on Wireless Communications and Networking | Full Text







.png)