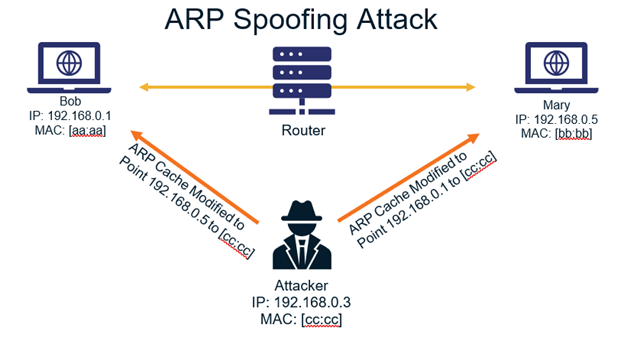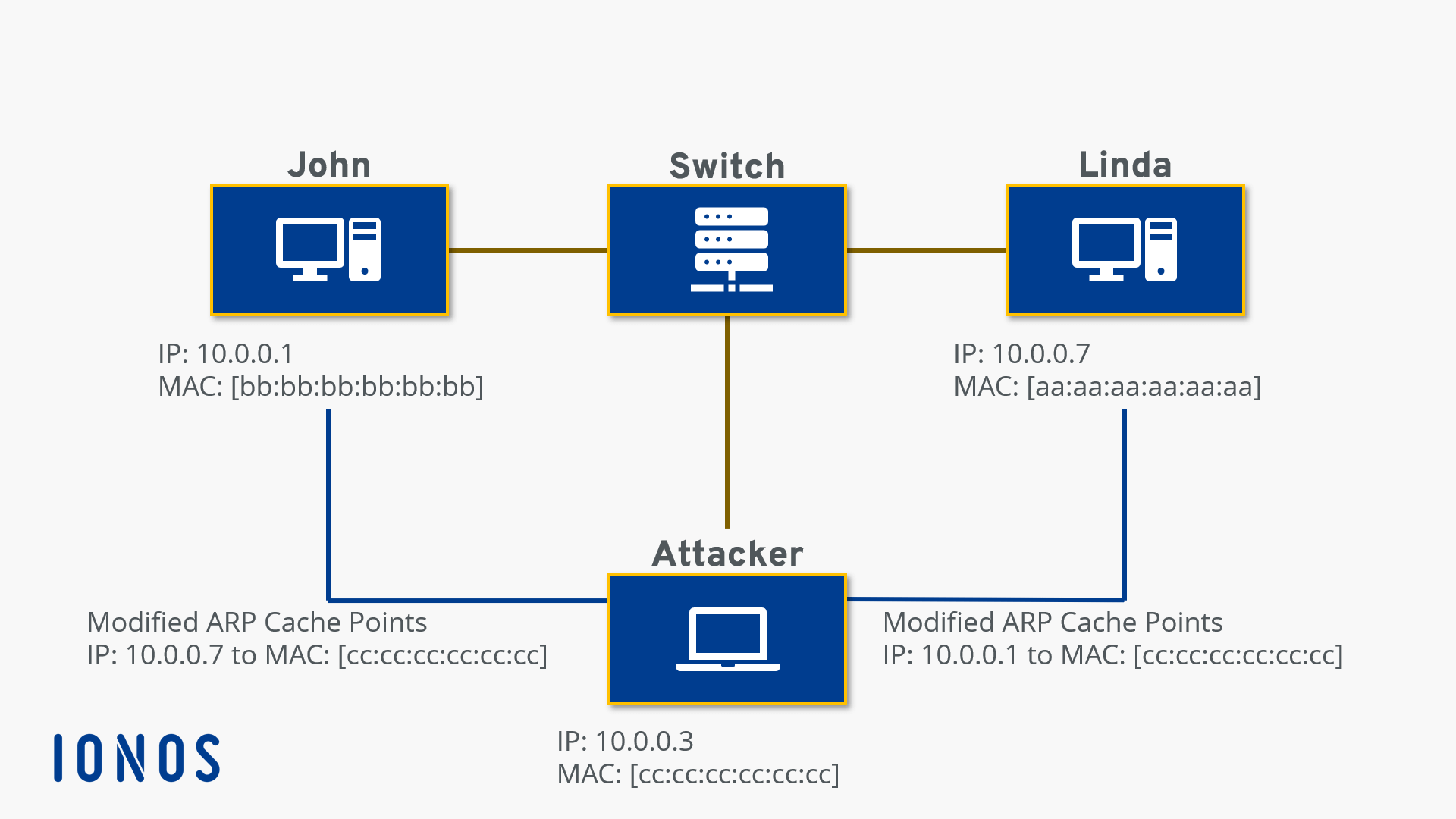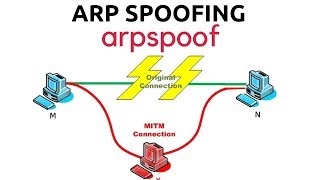
Electronics | Free Full-Text | Mitigating ARP Cache Poisoning Attack in Software-Defined Networking (SDN): A Survey | HTML

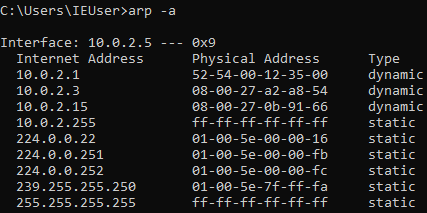
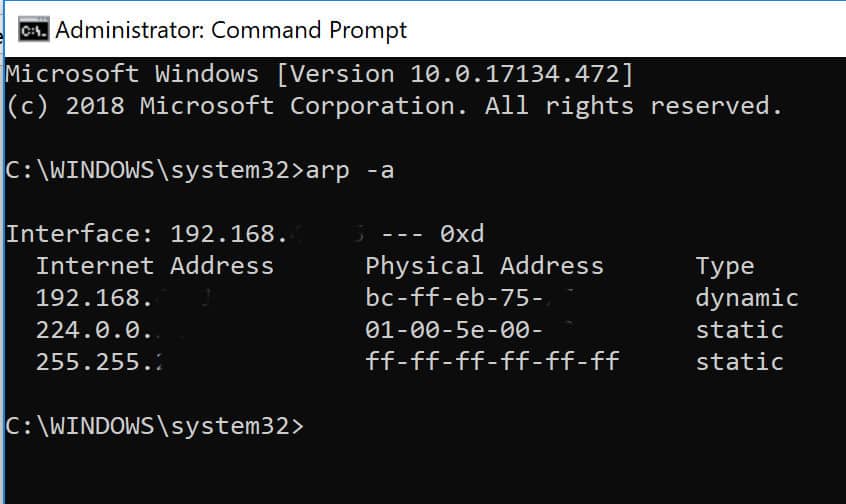
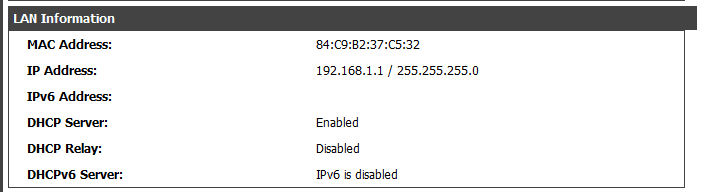
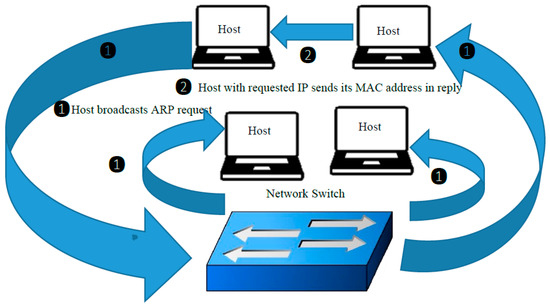
arp spoofing - An ARP table keeps multiple MAC addresses for an IP address or a single one? - Information Security Stack Exchange