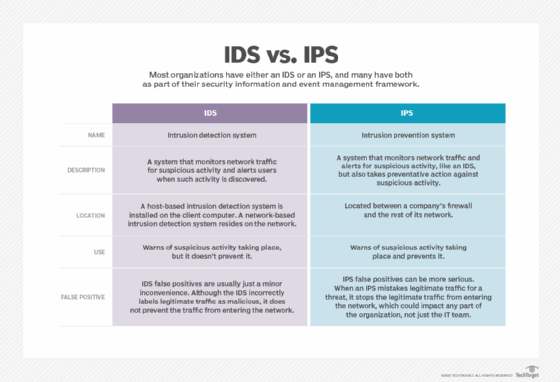
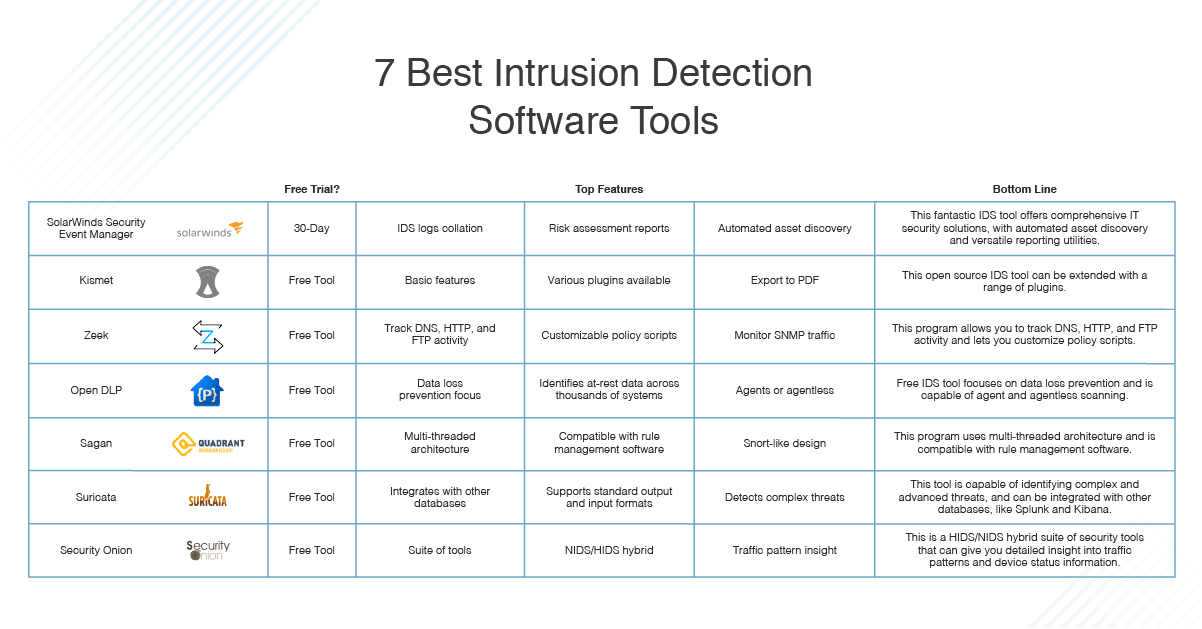
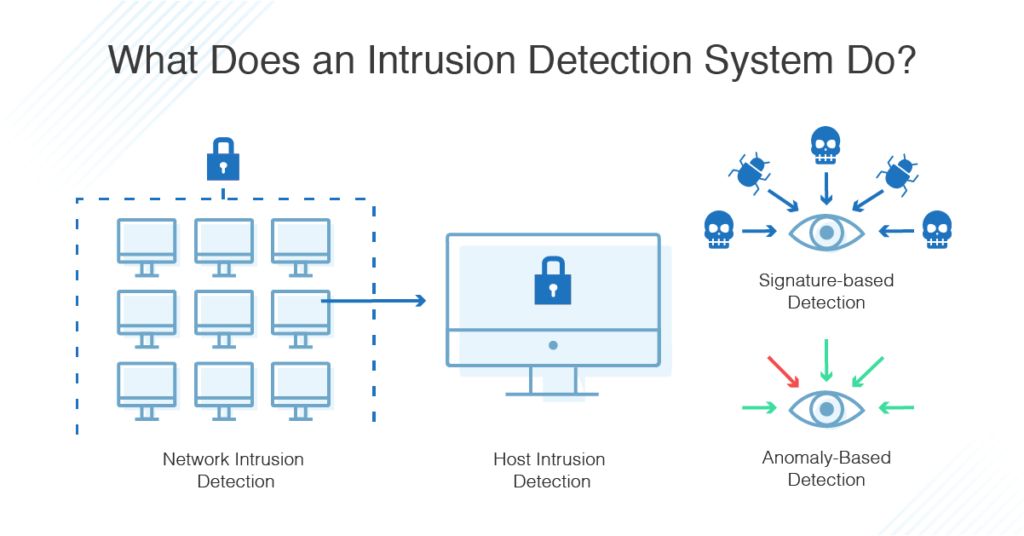
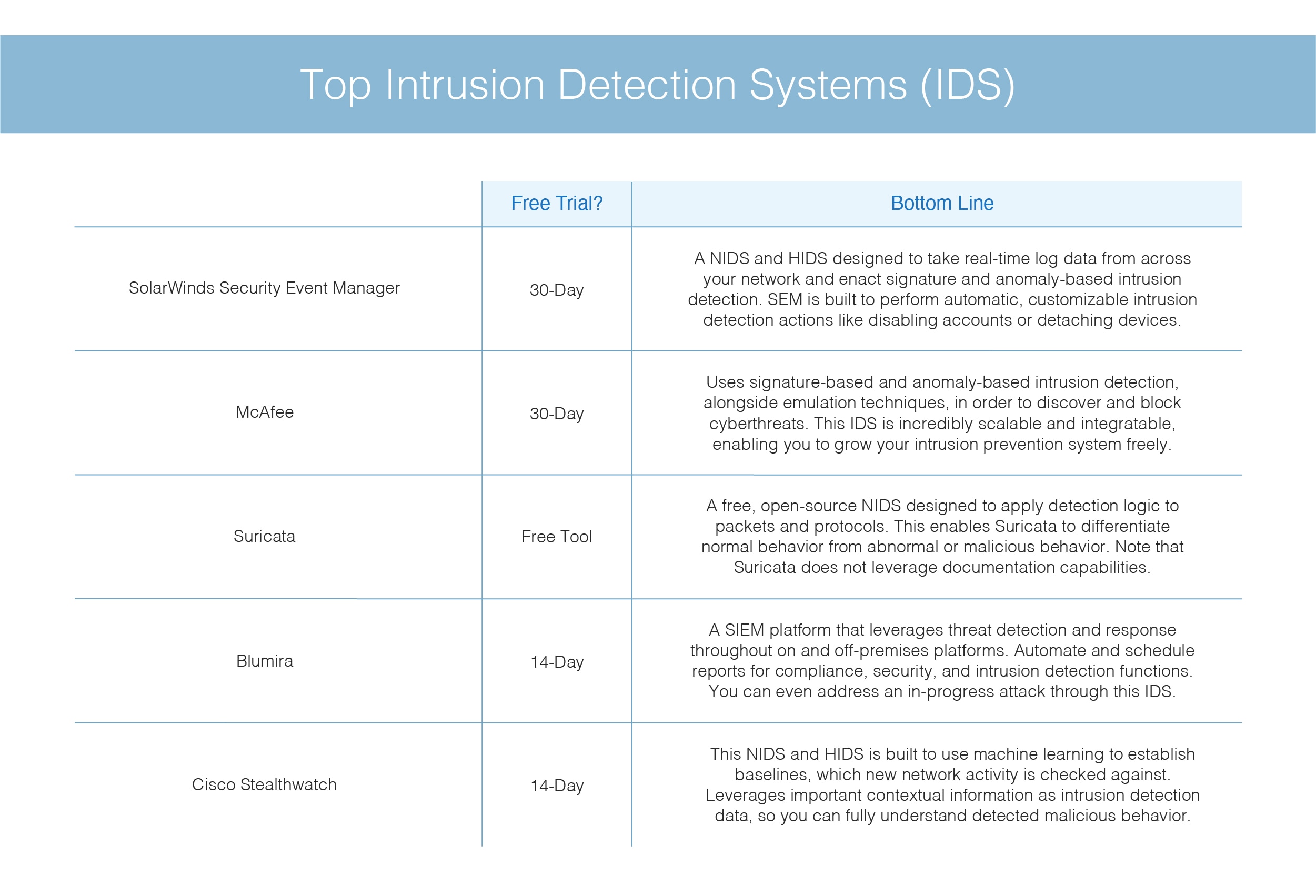
What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security

Network Intrusion Detection System. Network Intrusion Detection Basics Network intrusion detection systems are designed to sniff network traffic and. - ppt download

CERT issues advisory on nation wide cyber attack | OnlyTech Forums - Technology Discussion Community

What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security