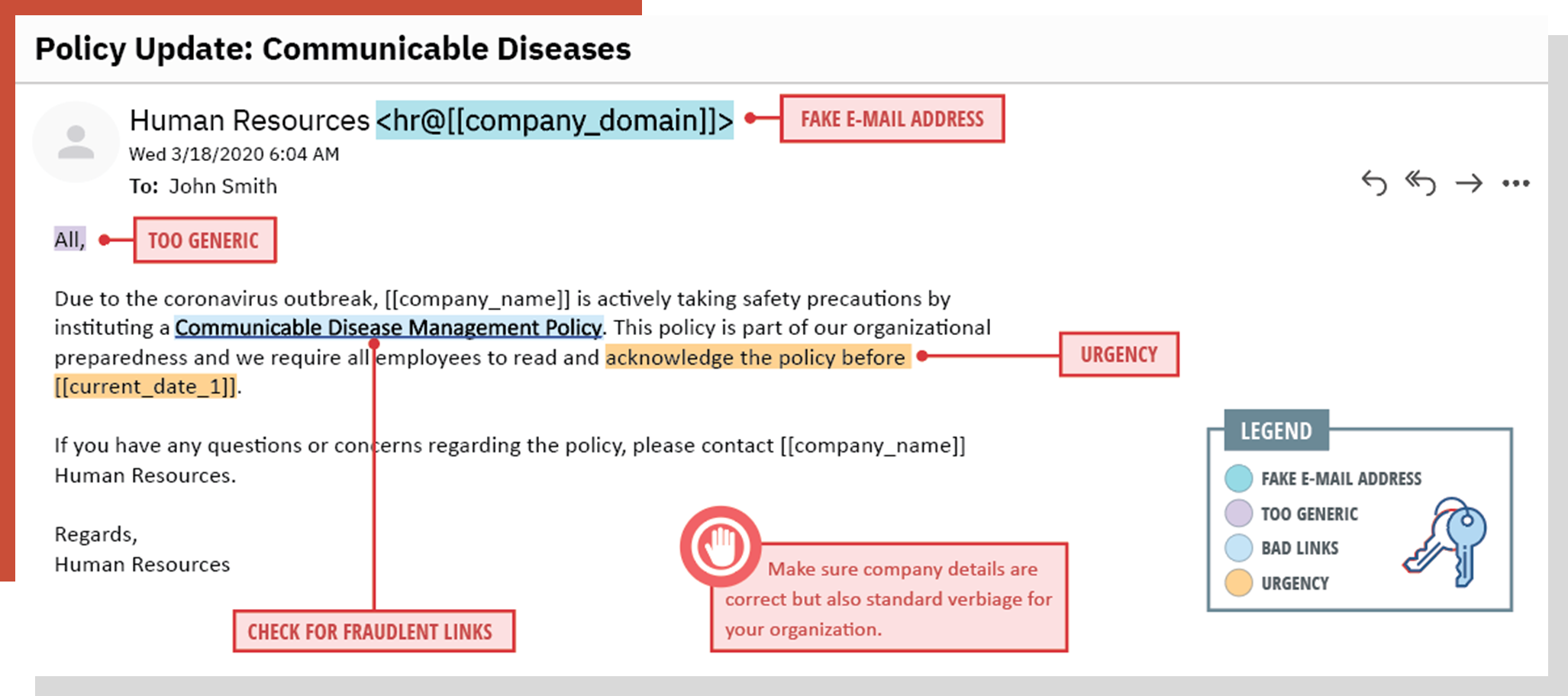
The Human Factor in IT Security: How Employees are Making Businesses Vulnerable from Within | Kaspersky official blog

The Human Factor in IT Security: How Employees are Making Businesses Vulnerable from Within | Kaspersky official blog

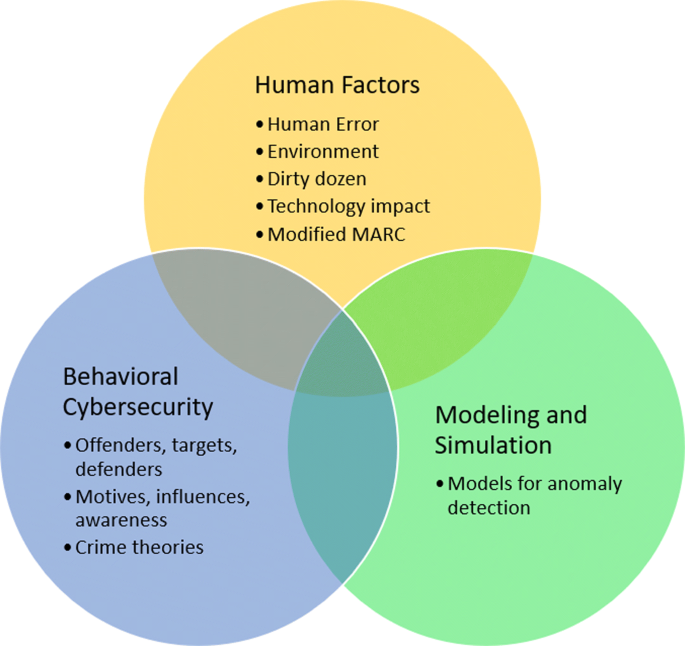
A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments - ScienceDirect

Gartner Predicts By 2025 Cyber Attackers Will Have Weaponized Operational Technology Environments to Successfully Harm or Kill Humans

Russian cyberattacks pose greater risk to governments and other insights from our annual report - Microsoft On the Issues

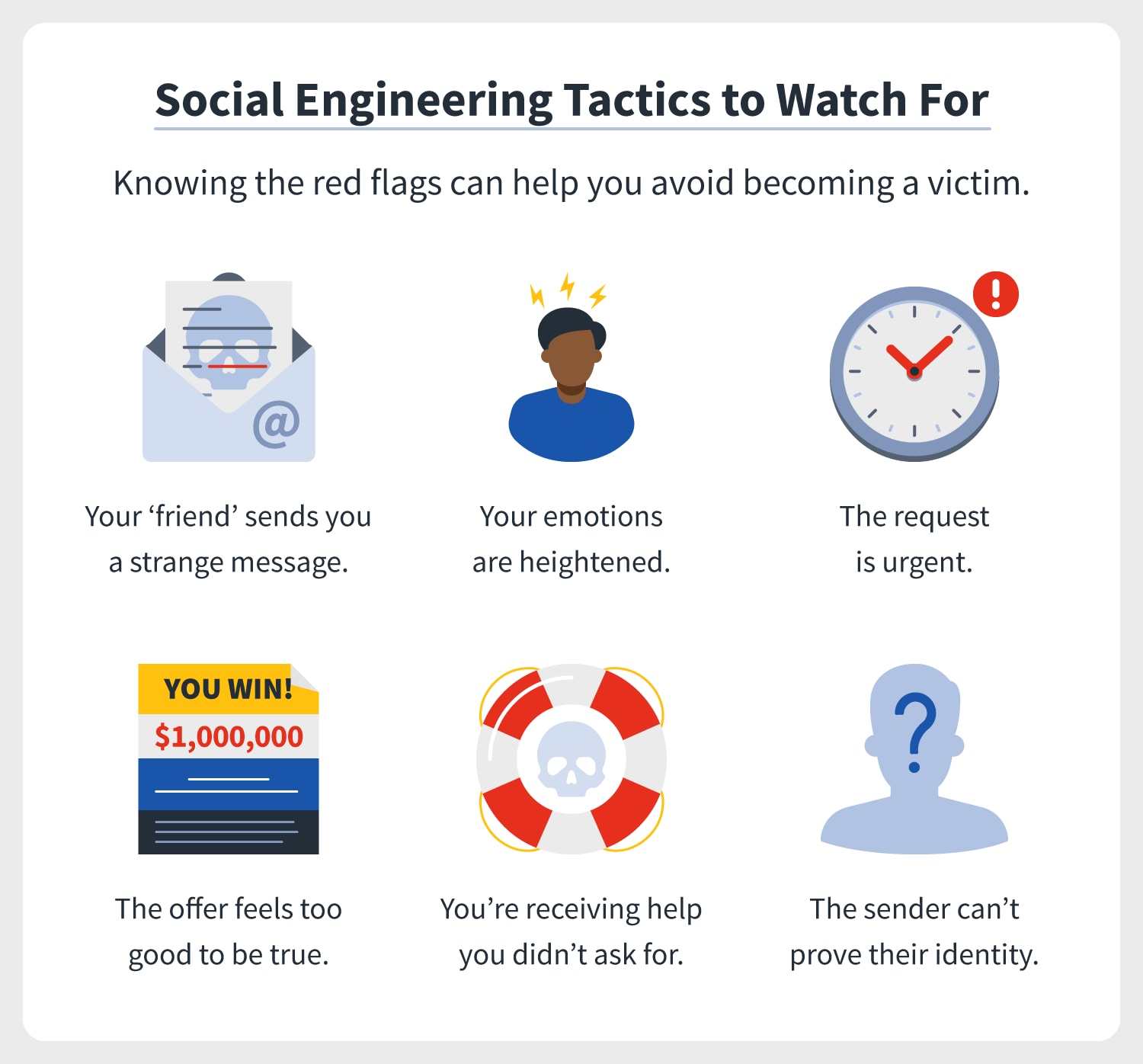





![166 Cybersecurity Statistics and Trends [updated 2022] 166 Cybersecurity Statistics and Trends [updated 2022]](https://142972.fs1.hubspotusercontent-na1.net/hub/142972/hubfs/blog%20posts/cybersecurity-compliance-by-company@2x.png?width=1384&name=cybersecurity-compliance-by-company@2x.png)
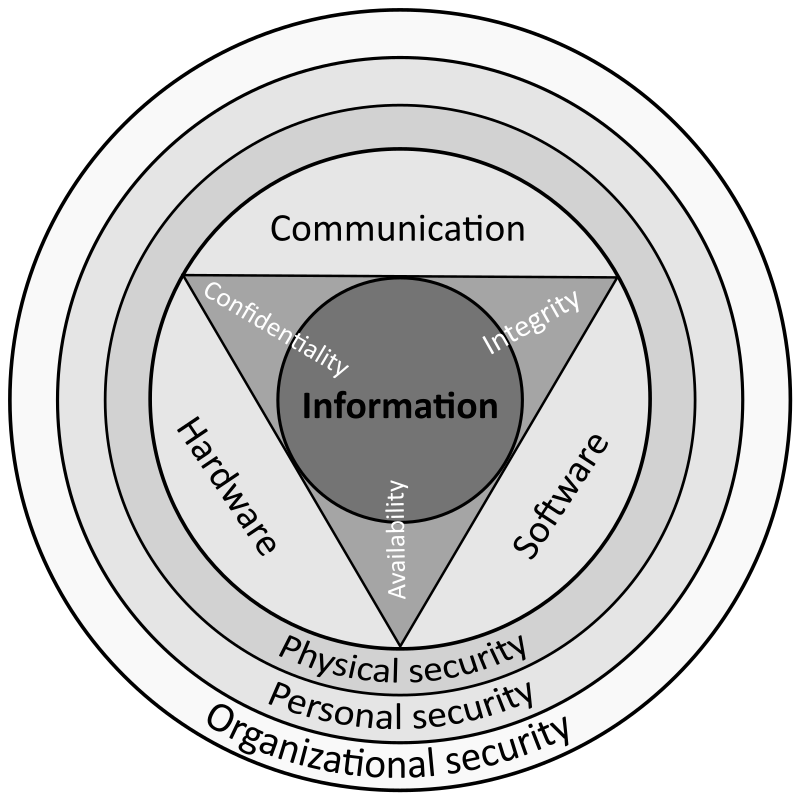
![Cybersecurity Best Practices for 2022 [15 Data Protection Methods] | Ekran System Cybersecurity Best Practices for 2022 [15 Data Protection Methods] | Ekran System](https://www.ekransystem.com/sites/default/files/15%20best%20cybersecurity%20practices/open-15-graph-Cybersecurity-Best-Practices-to-Prevent-Cyber-Attacks-in-2022.jpg)