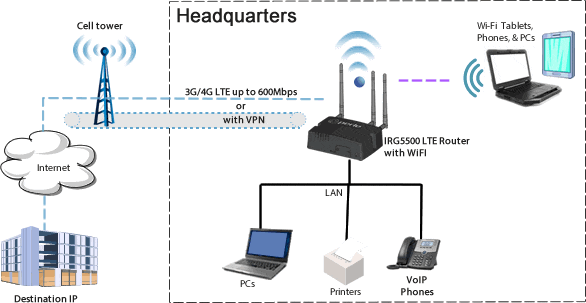
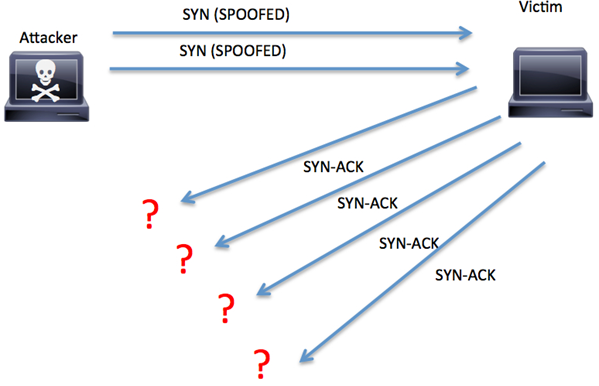
denial of service - How could a SYN flood affect a home router - Information Security Stack Exchange
TCP SYN Flood Attack - Router IP - ESET Internet Security & ESET Smart Security Premium - ESET Security Forum

Celcom offers to replace flood-damaged broadband routers for free | Malay Mail – Malay News- Malaysian newspapers from Kuala Lumpur