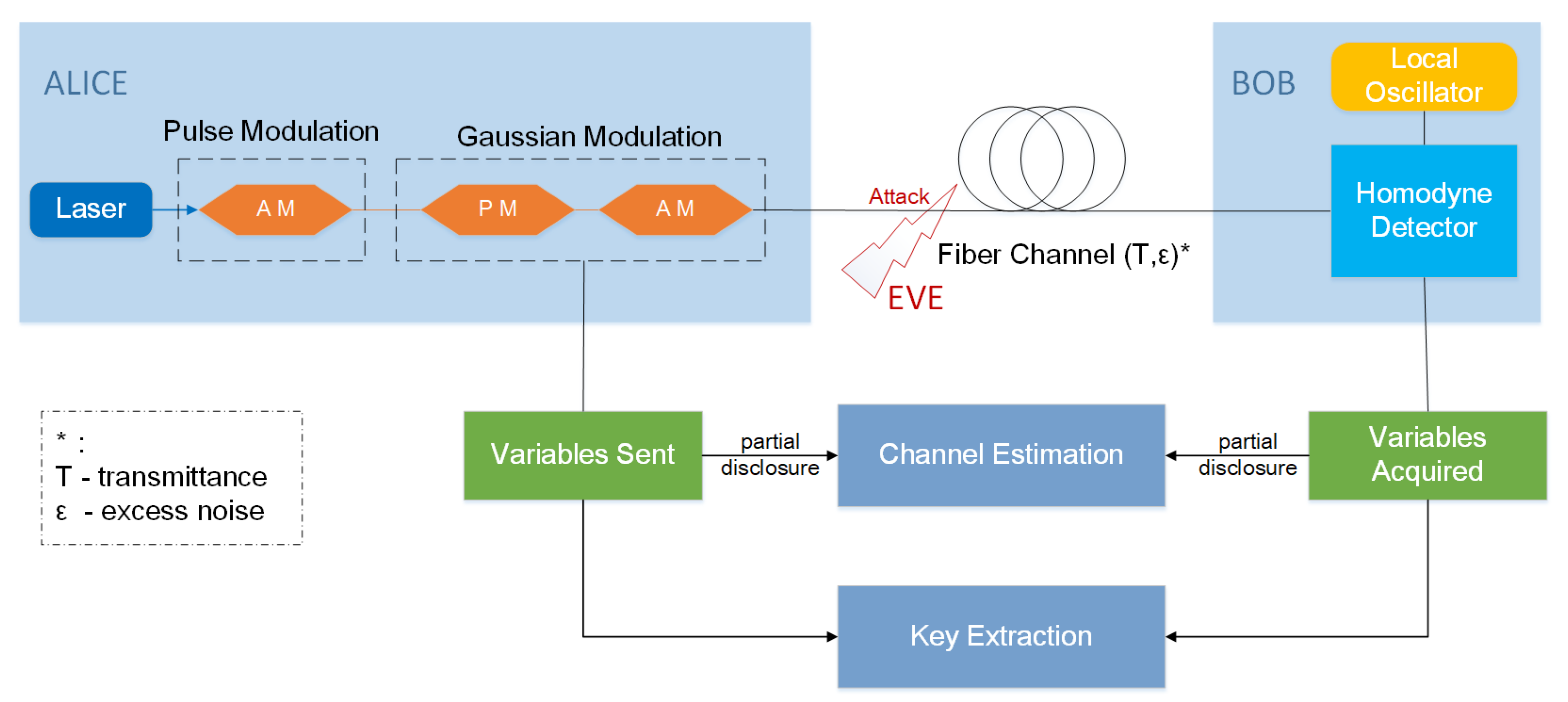
Photonics | Free Full-Text | Low-Rate Denial-of-Service Attack Detection: Defense Strategy Based on Spectral Estimation for CV-QKD | HTML
GitHub - pablocelayes/rsa-wiener-attack: A Python implementation of the Wiener attack on RSA public-key encryption scheme.


![PDF] On the Improvement of Wiener Attack on RSA with Small Private Exponent | Semantic Scholar PDF] On the Improvement of Wiener Attack on RSA with Small Private Exponent | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2c5c7ae179350b71361bf93f9a00d4f8f073f6a6/6-Table1-1.png)


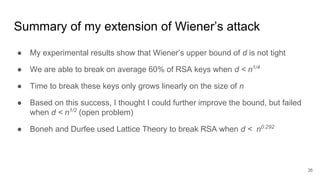
![Weak RSA [easy]: HackTheBox Crypto Challenge (wieners attack) - YouTube Weak RSA [easy]: HackTheBox Crypto Challenge (wieners attack) - YouTube](https://i.ytimg.com/vi/M-yg0vbrAOk/maxresdefault.jpg)