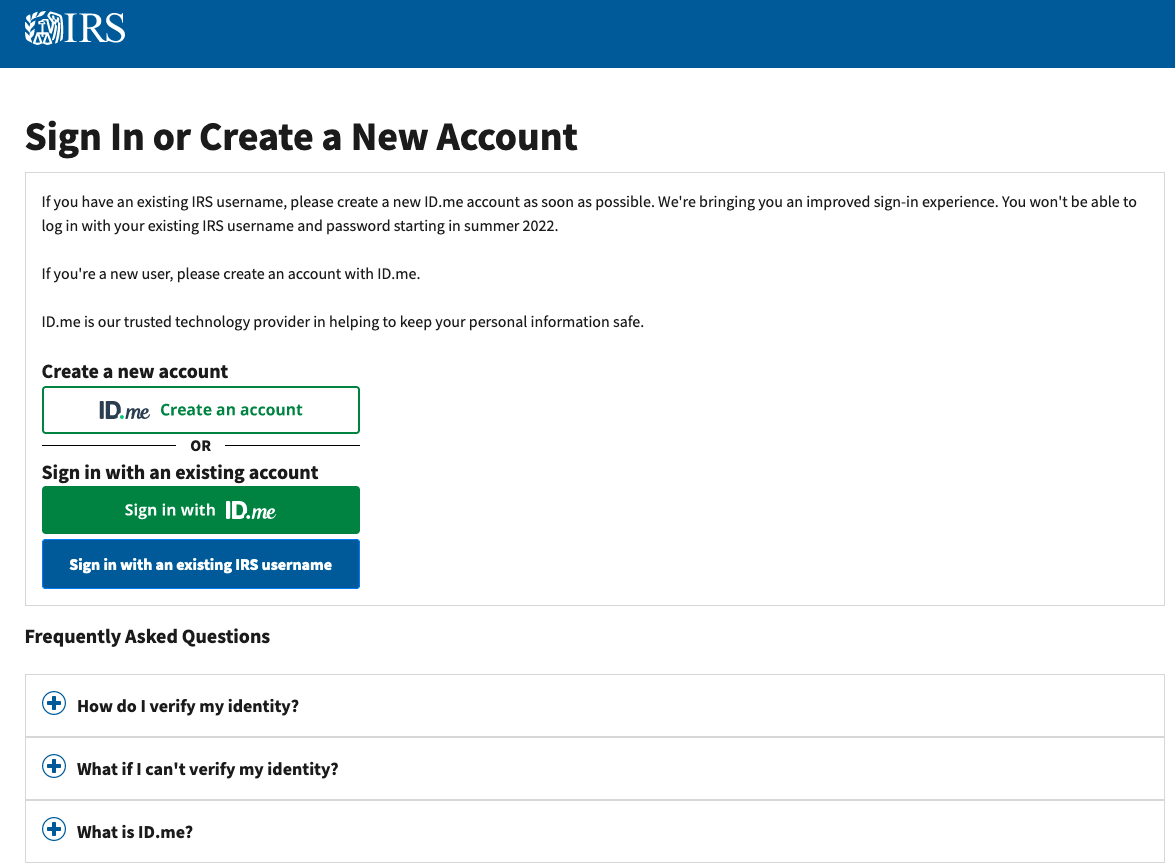
A Double-blinded, Randomized, Placebo-controlled Trial of Antibiotic Prophylaxis in Elective Non-hysterectomy Laparoscopic Surgery for Benign Gynecologic Conditions: A Pilot Study - Journal of Minimally Invasive Gynecology

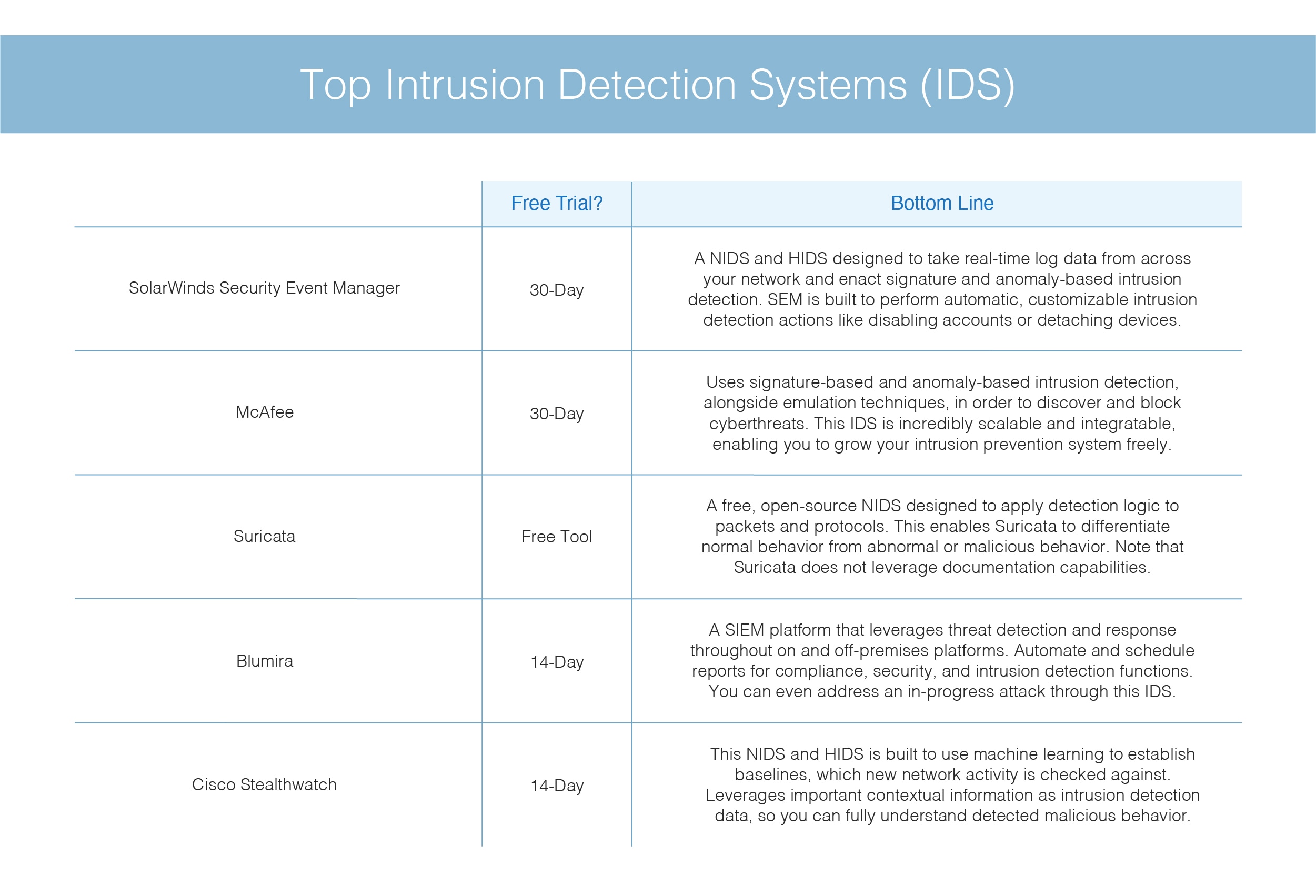
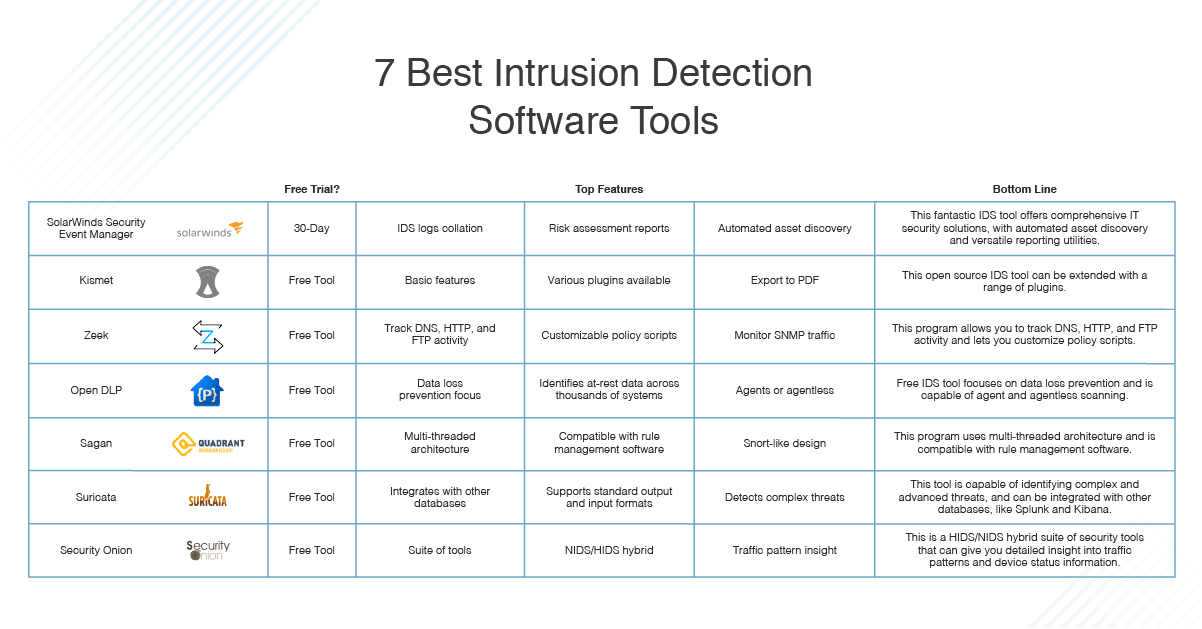
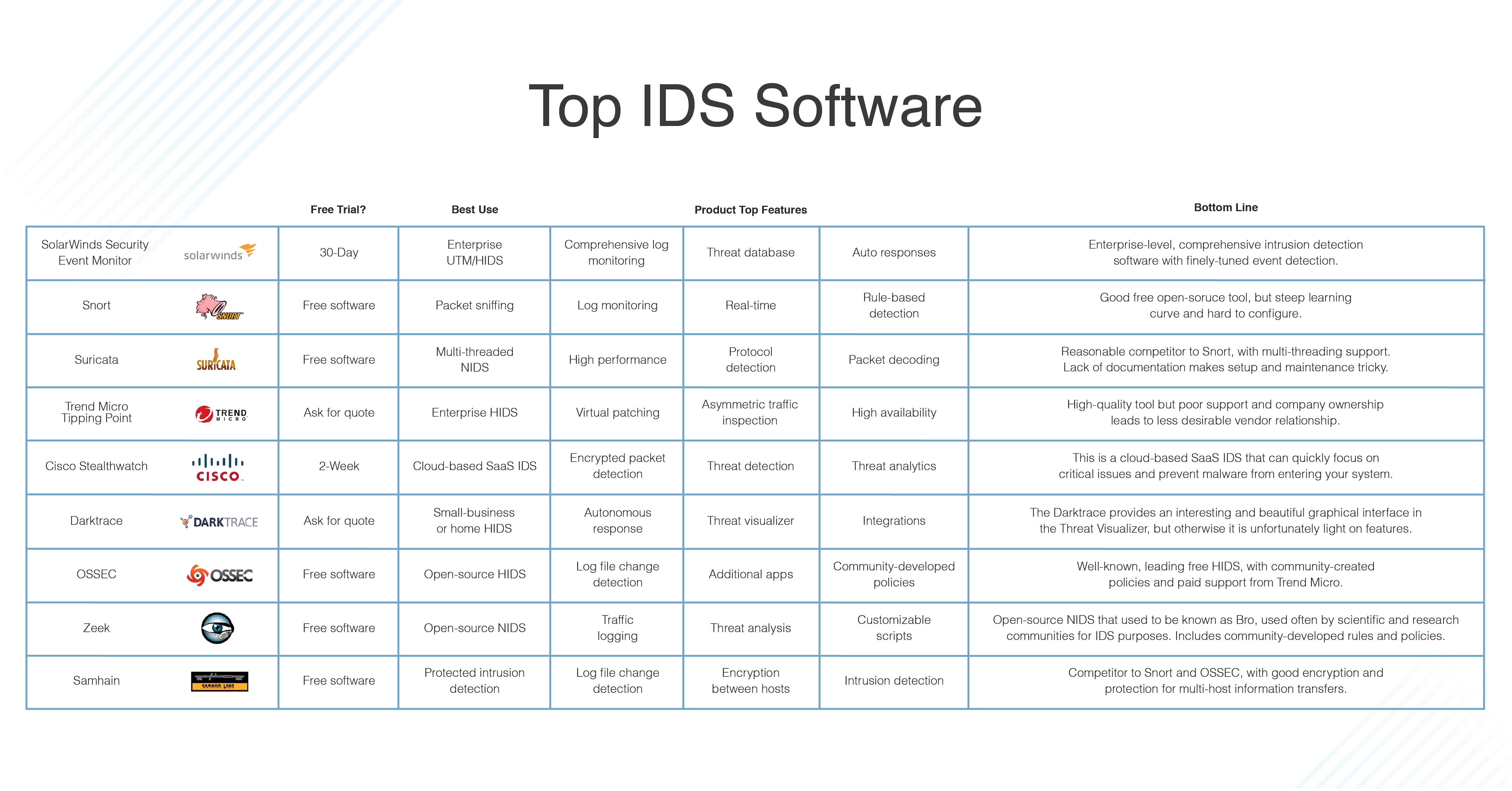
What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security

What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security
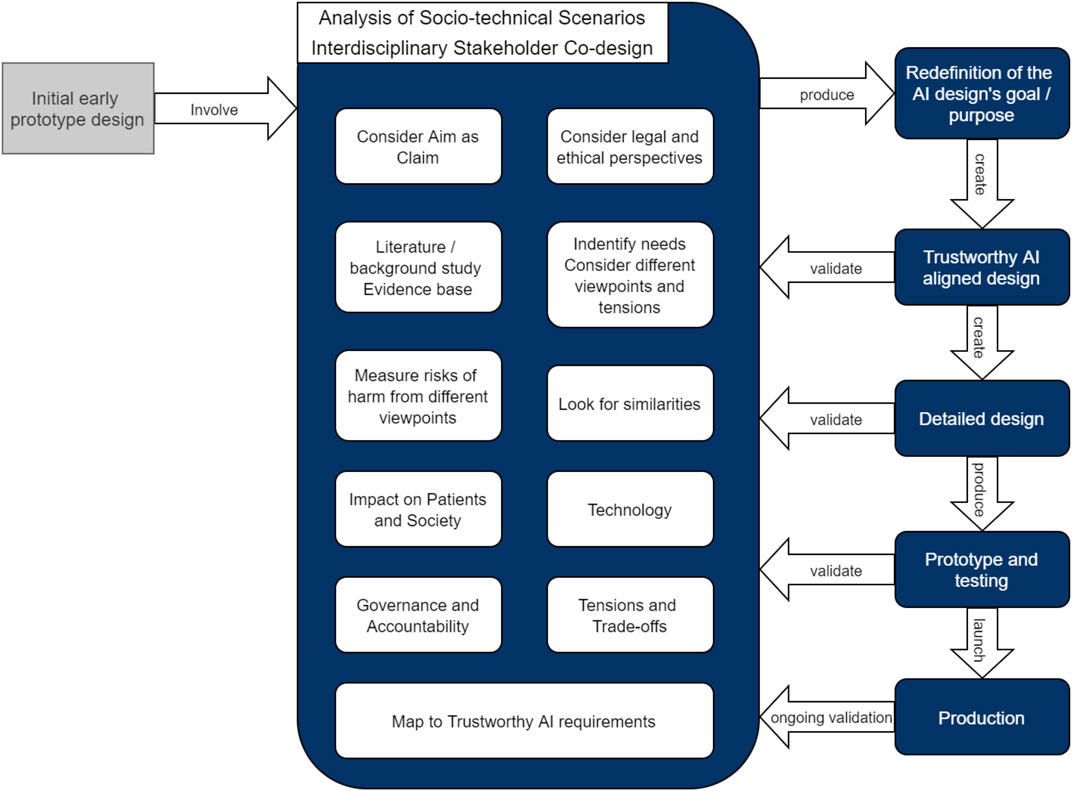
Frontiers | Co-Design of a Trustworthy AI System in Healthcare: Deep Learning Based Skin Lesion Classifier

Electronics | Free Full-Text | Toward Developing Efficient Conv-AE-Based Intrusion Detection System Using Heterogeneous Dataset | HTML
![Cisco IOS XR System Monitoring Configuration Guide for the Cisco CRS Router, Release 6.1.x - Implementing and Monitoring Alarms and Alarm Log Correlation [Cisco IOS XR Software (End-of-Sale)] - Cisco Cisco IOS XR System Monitoring Configuration Guide for the Cisco CRS Router, Release 6.1.x - Implementing and Monitoring Alarms and Alarm Log Correlation [Cisco IOS XR Software (End-of-Sale)] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/100001-200000/110001-120000/117001-118000/117361.eps/_jcr_content/renditions/117361.jpg)
Cisco IOS XR System Monitoring Configuration Guide for the Cisco CRS Router, Release 6.1.x - Implementing and Monitoring Alarms and Alarm Log Correlation [Cisco IOS XR Software (End-of-Sale)] - Cisco
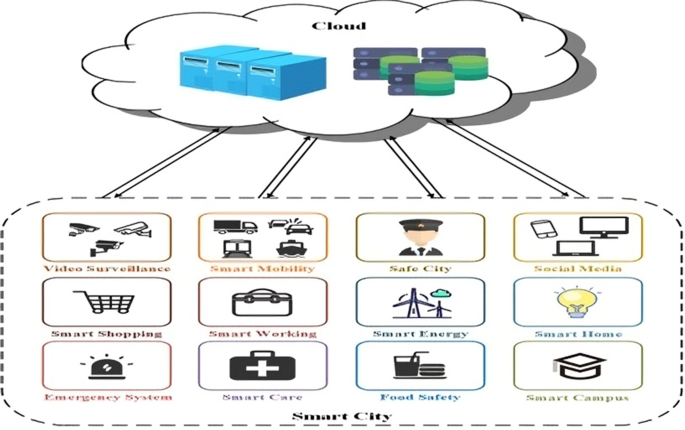
Design of Intrusion Detection System based on Cyborg intelligence for security of Cloud Network Traffic of Smart Cities | Journal of Cloud Computing | Full Text

What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security

Direct Challenges for the Evaluation of Beta-Lactam Allergy: Evidence and Conditions for Not Performing Skin Testing - The Journal of Allergy and Clinical Immunology: In Practice