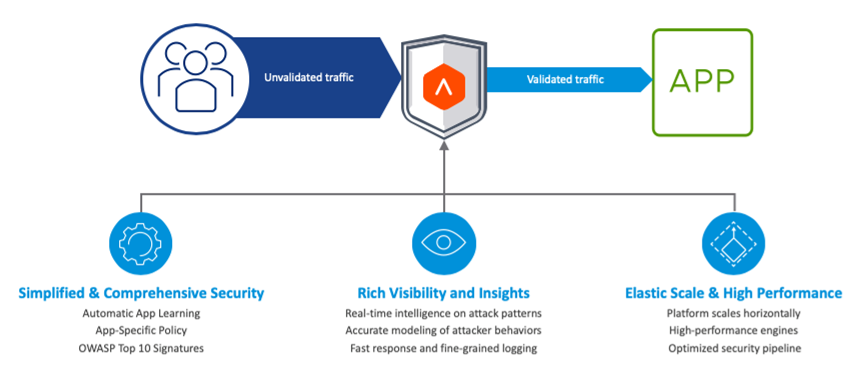
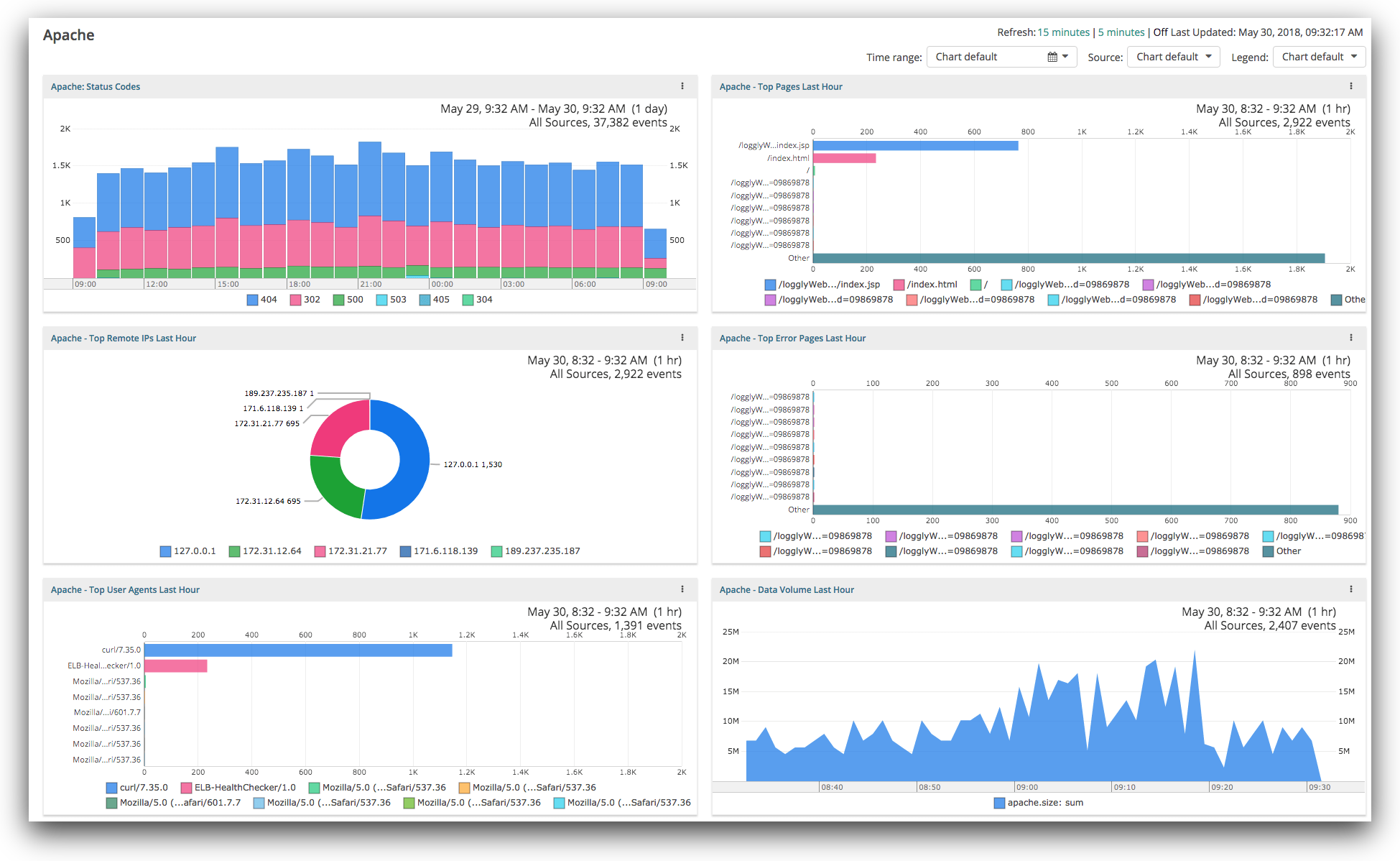
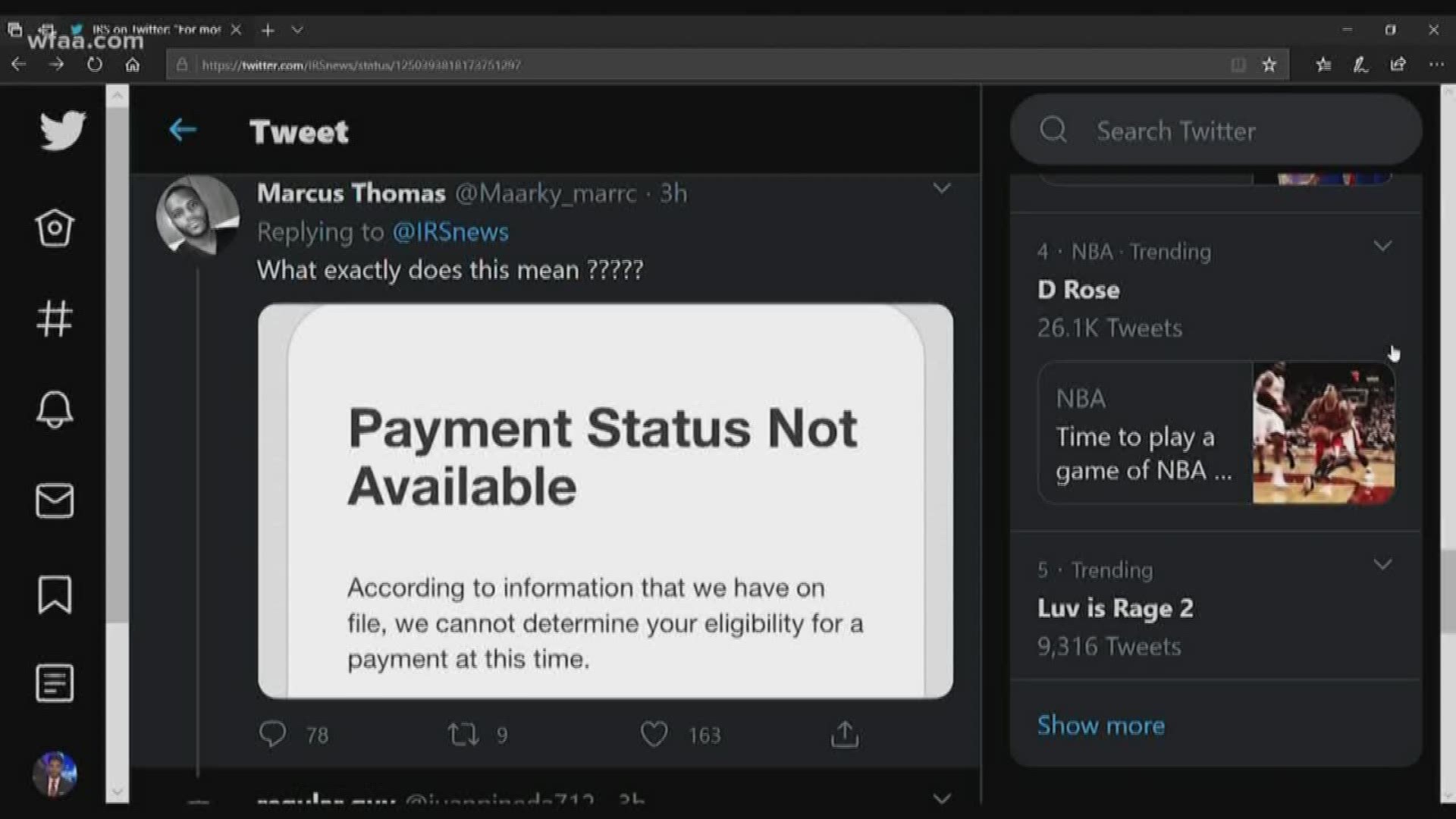
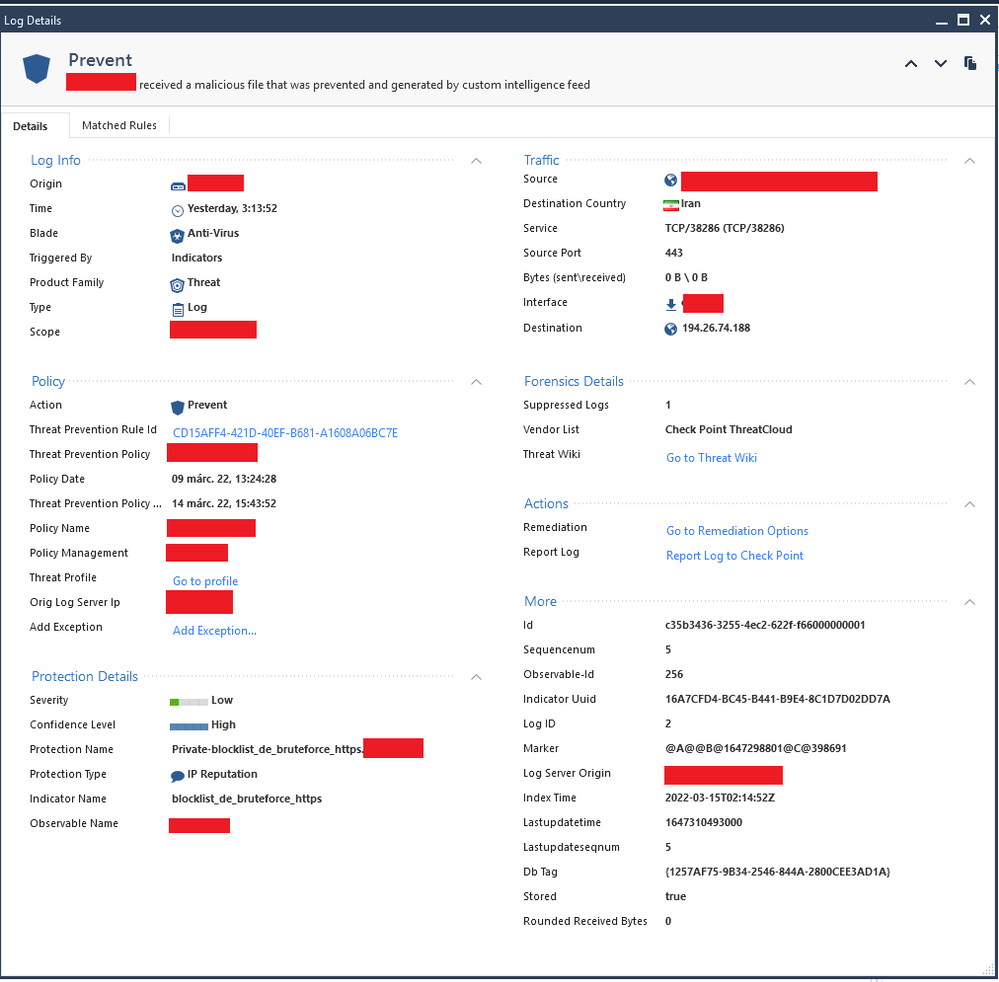
High-level overview: Traffic samples are collected offline and then... | Download Scientific Diagram

Want To Log Your Access Requests? Here's How You Can Optimize Multiple Databases in Rails 6! – Josh Software

Automation to block malicious flows detected by Azure Traffic Analytics | by James Dumont le Douarec | Microsoft Azure | Medium

Enterprise Application Logging Best Practices (A Support Engineer's Perspective) | by Thilina Ashen Gamage | Better Programming

InApp Mysql VS Azure Database for MySQL Which one is faster for Woocommerce Wordpress website ? - Microsoft Q&A