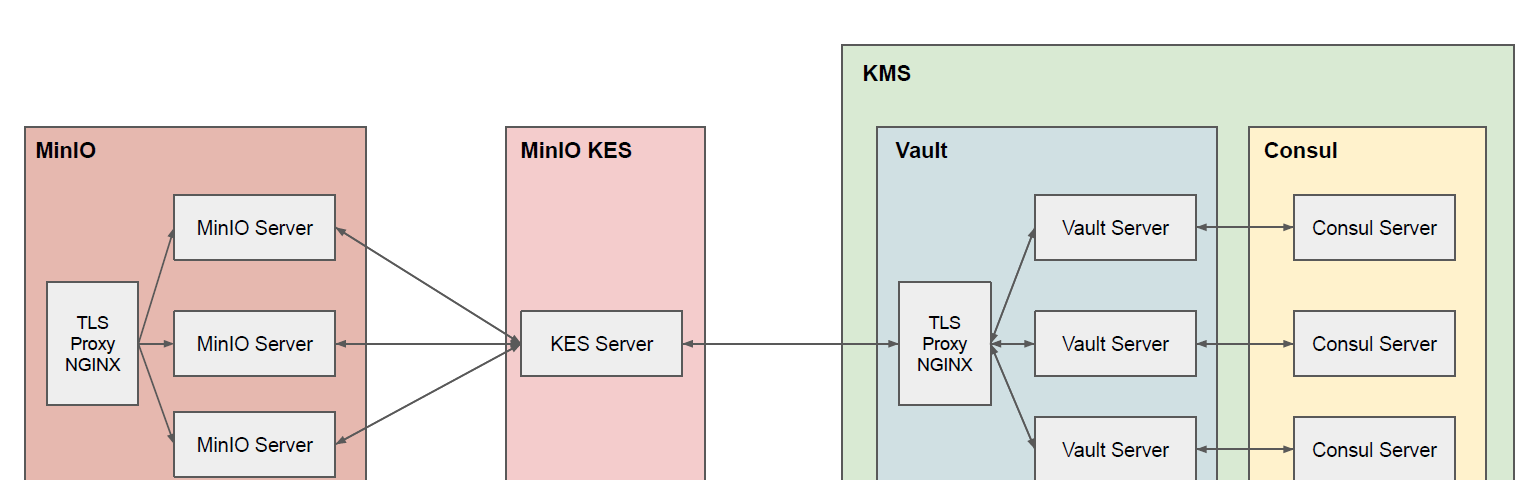
Proxy Re-Encryption — Allowing Alice To Share Her Protect Secret Key With Bob | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
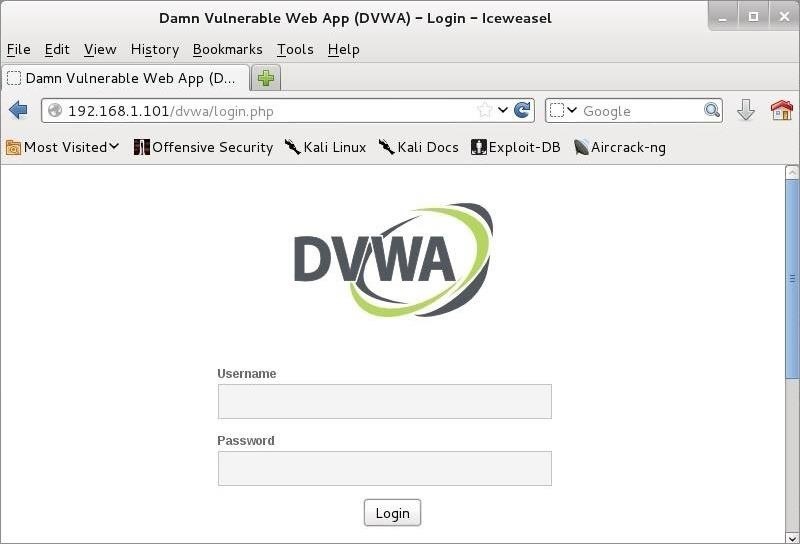
Hack Like a Pro: How to Crack Online Web Form Passwords with THC-Hydra & Burp Suite « Null Byte :: WonderHowTo

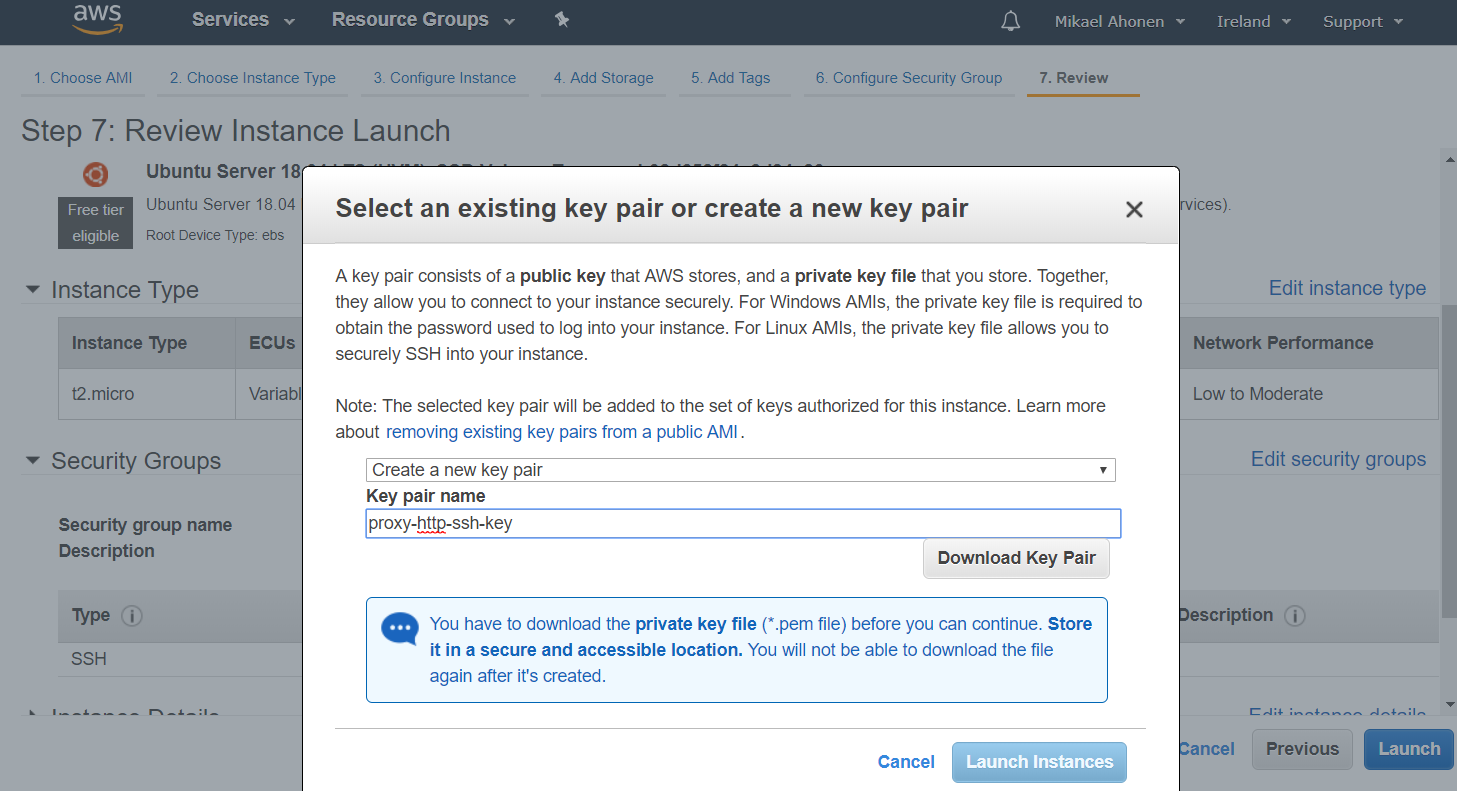
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members
![NEW PROXO PET SIM X) [🏦 BANK] PET SIMULATOR X SCRIPT PASTEBIN!|UNLOCK ALL GAMEPASS AUTOFARM - YouTube NEW PROXO PET SIM X) [🏦 BANK] PET SIMULATOR X SCRIPT PASTEBIN!|UNLOCK ALL GAMEPASS AUTOFARM - YouTube](https://i.ytimg.com/vi/mdKgGh6xSlI/hqdefault.jpg)
NEW PROXO PET SIM X) [🏦 BANK] PET SIMULATOR X SCRIPT PASTEBIN!|UNLOCK ALL GAMEPASS AUTOFARM - YouTube