I͛P͛h͛o͛n͛e͛G͛a͛l͛a͛x͛y͛M͛D͛ 11K͛ 🏴☠️ on Twitter: "Rainbow table attack #attack #attacks #cyber #cybersecurity #cyberattack #hash #table #hashing #hac #hacks #hack #hacker #hacked #hacker #hackers #hacking #ddos #awareness #aware #safe #security ...

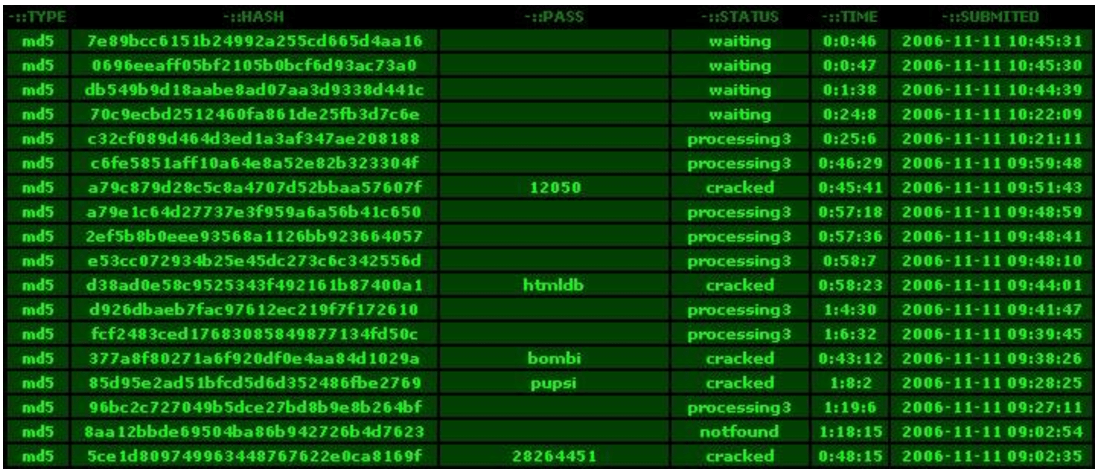
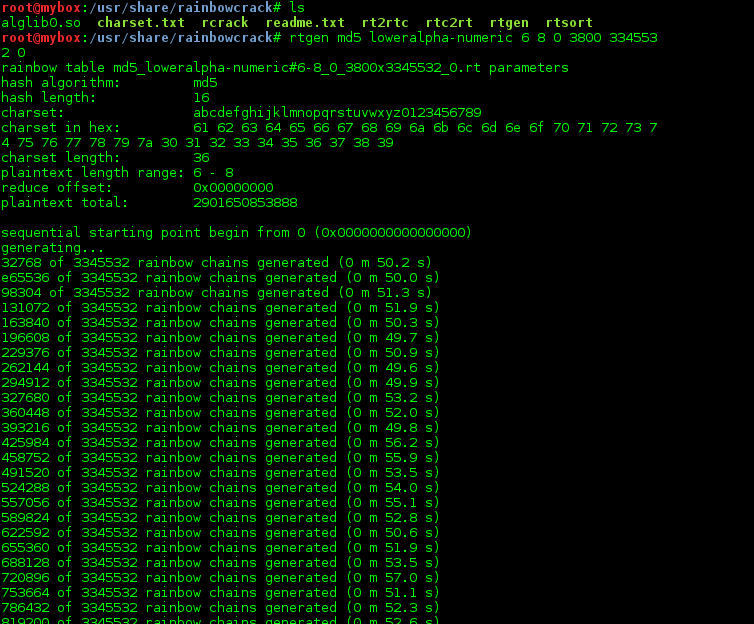
How to Create Rainbow Tables for Hashing Algorithms Like MD5, SHA1 & NTLM « Null Byte :: WonderHowTo
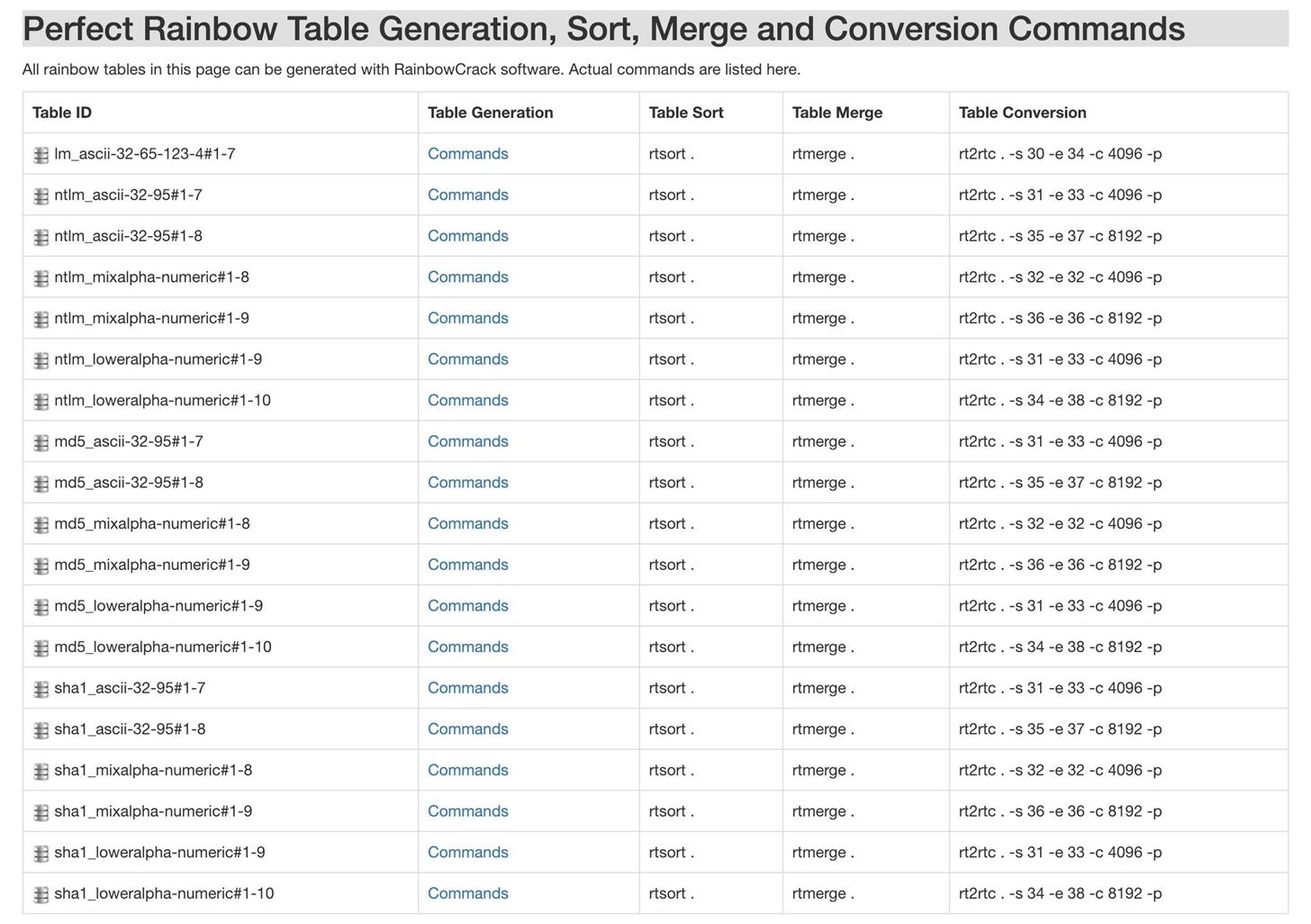
How to Create Rainbow Tables for Hashing Algorithms Like MD5, SHA1 & NTLM « Null Byte :: WonderHowTo

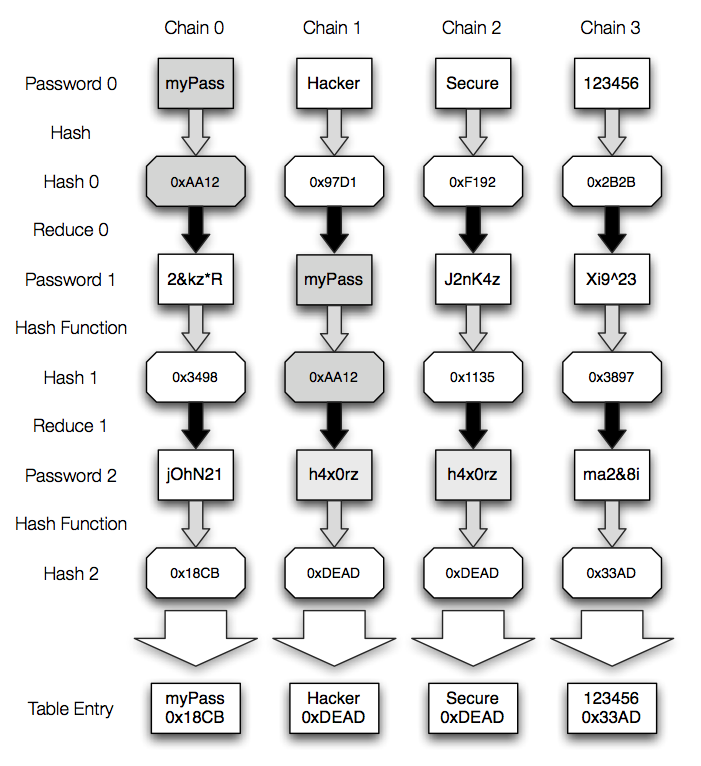
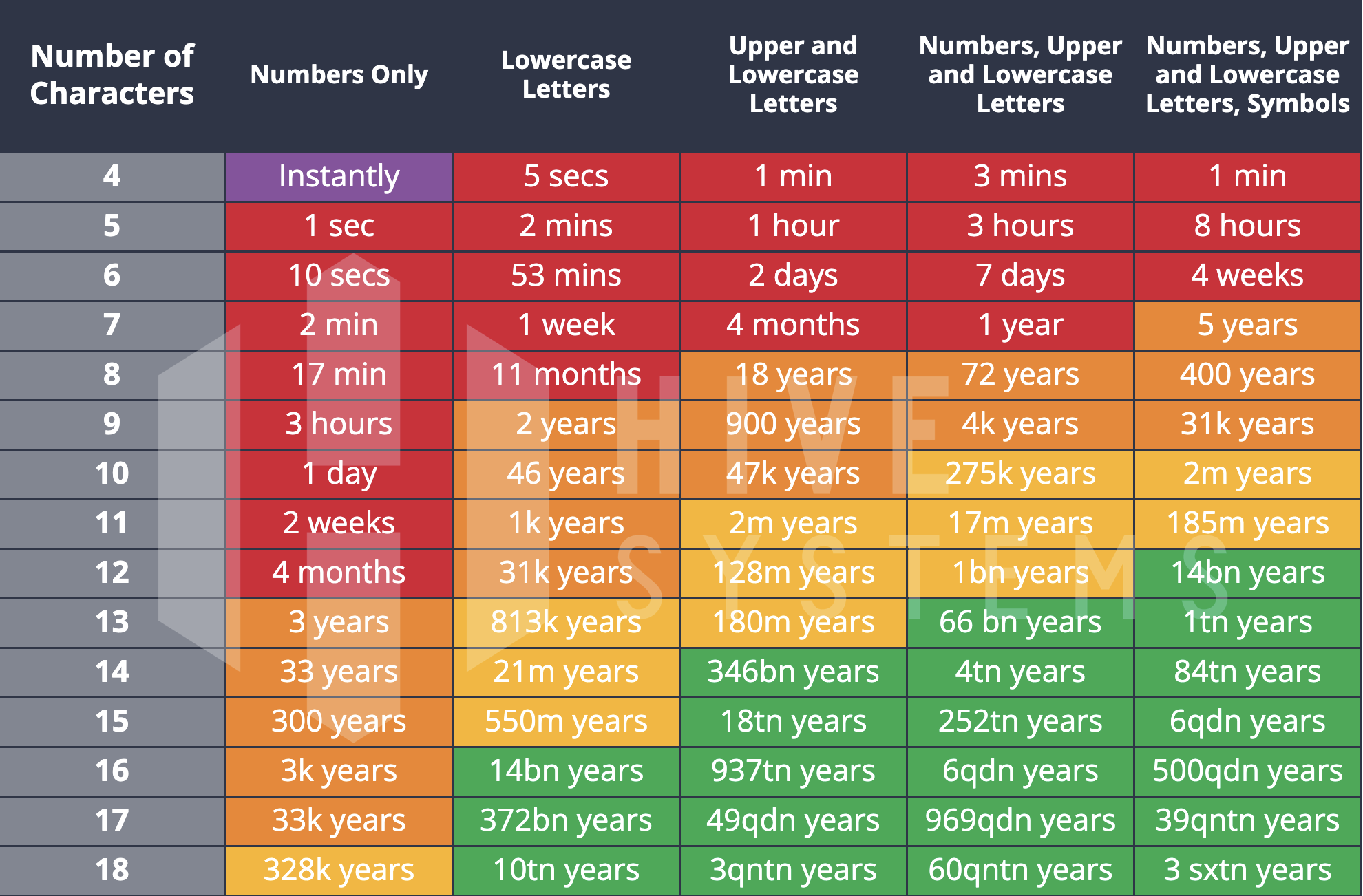
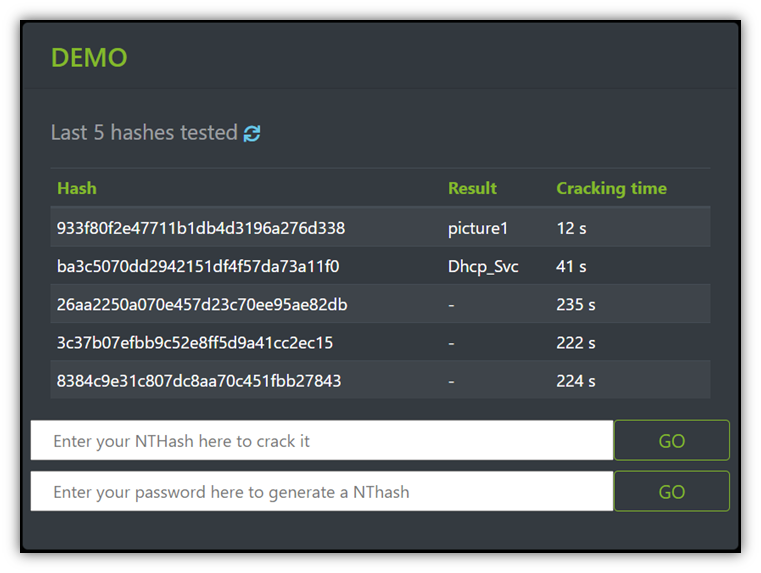
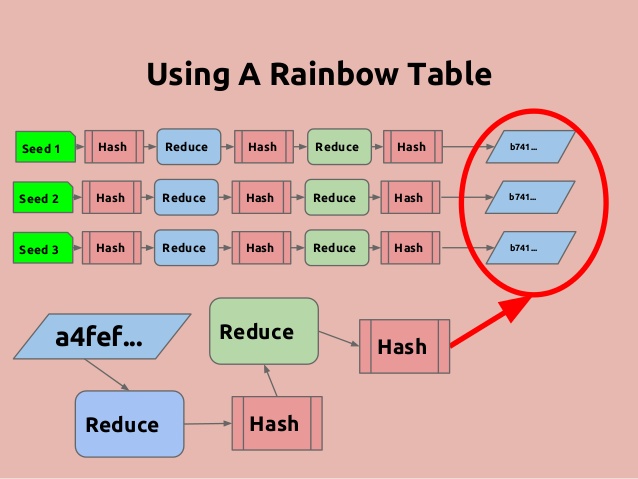
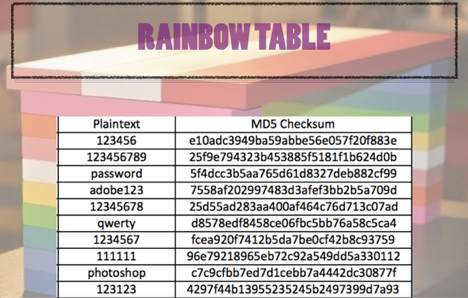
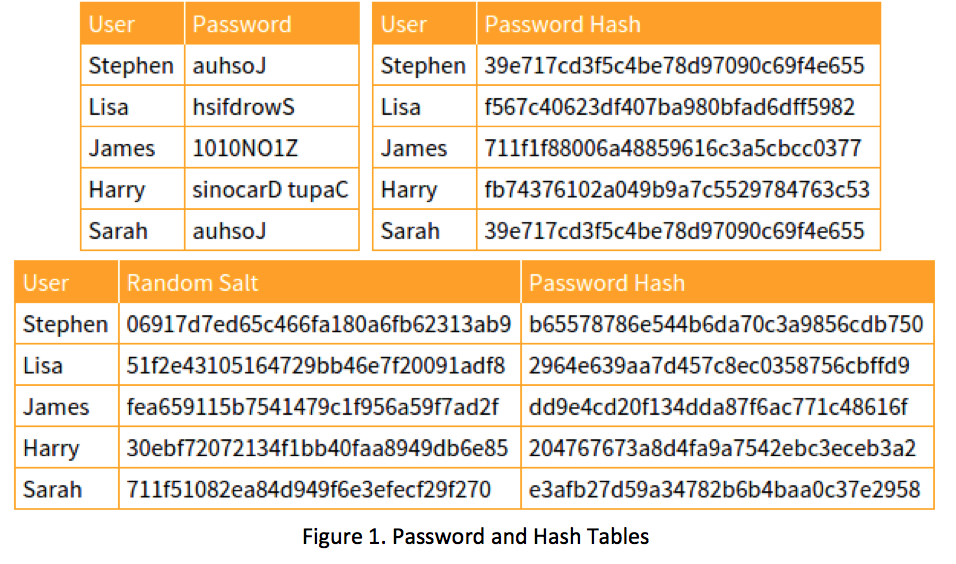
Magic Password - What is a rainbow table attack? It is a type of hacking wherein the hacker tries to use a rainbow hash table to crack the passwords stored in a

International College For Security Studies - ICSS - A rainbow table attack is a type of hacking wherein the perpetrator tries to use a rainbow hash table to crack the passwords stored