Symmetry | Free Full-Text | Homomorphic Comparison for Point Numbers with User-Controllable Precision and Its Applications

PDF) A killer application for pairings: authenticated key establishment in underwater wireless sensor networks | Rodrigo Roman - Academia.edu

A Lightweight Proxy Re-Encryption Approach with Certificate-Based and Incremental Cryptography for Fog-Enabled E-Healthcare
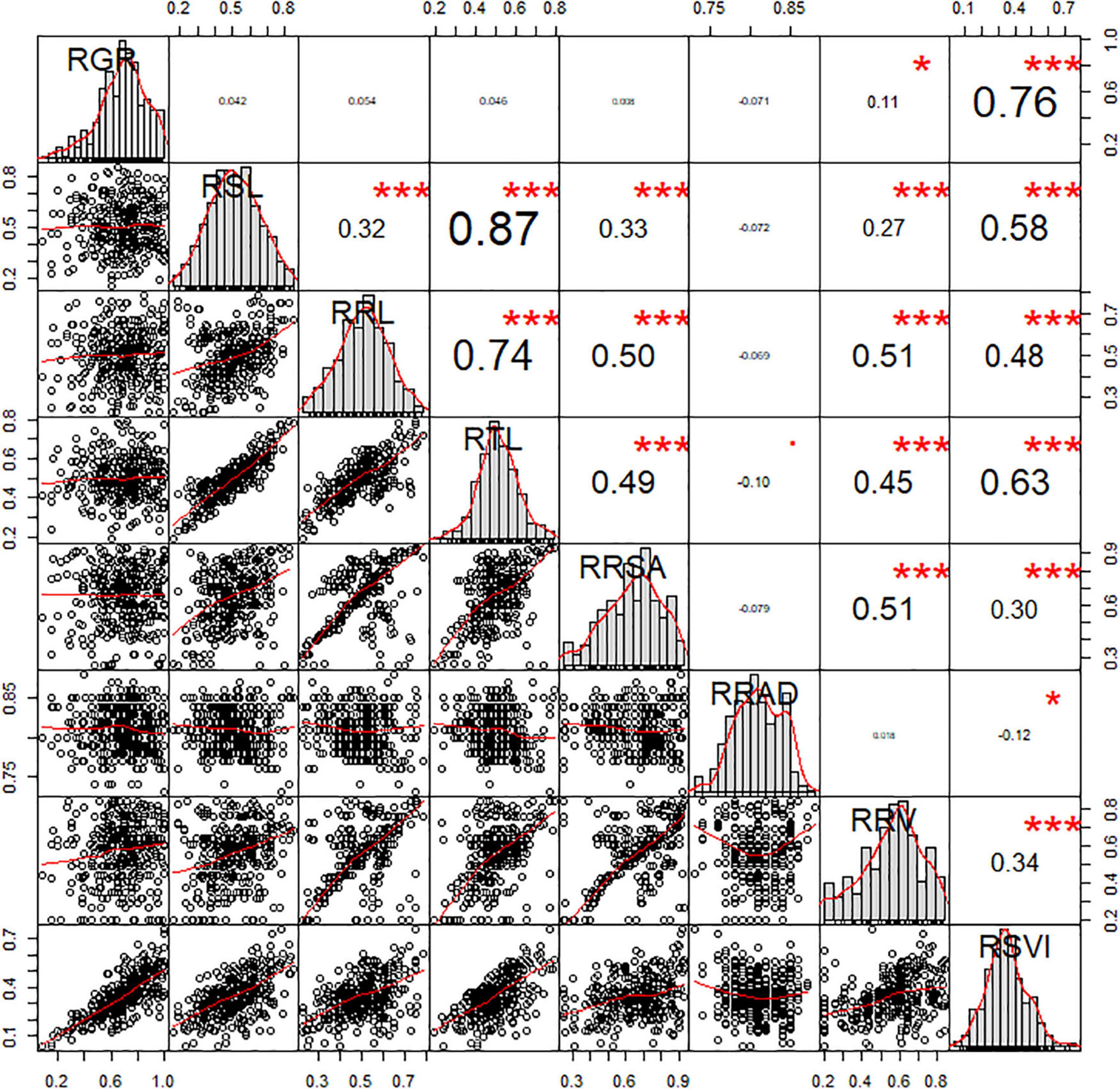
Frontiers | Using a high density bin map to analyze quantitative trait locis of germination ability of maize at low temperatures

CTJV801 A Practical Public Key Encryption Scheme Based On Learning Parity With Noise | PDF | Cryptography | Key (Cryptography)
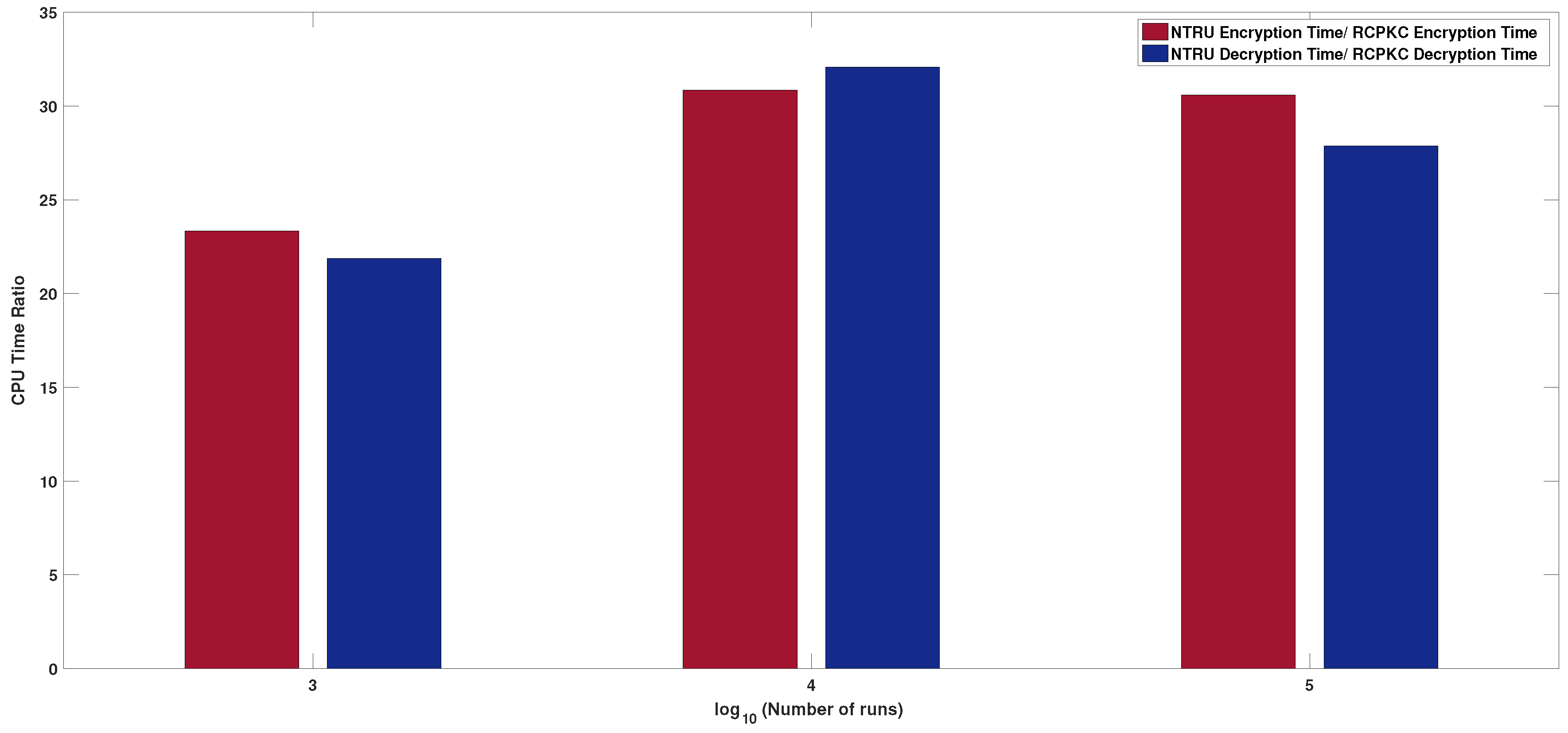
Sensors | Free Full-Text | NTRU-Like Random Congruential Public-Key Cryptosystem for Wireless Sensor Networks